From 4dce0e59585337ef4ea4af8aa2a2bf2bfb52cad0 Mon Sep 17 00:00:00 2001
From: Pol Henarejos <55573252+polhenarejos@users.noreply.github.com>
Date: Mon, 13 Jun 2022 14:33:33 +0200
Subject: [PATCH] Update public_key_authentication.md
Added screenshots.
---
doc/public_key_authentication.md | 19 ++++++++++++++++---
1 file changed, 16 insertions(+), 3 deletions(-)
diff --git a/doc/public_key_authentication.md b/doc/public_key_authentication.md
index 25b389f..a24c4cf 100644
--- a/doc/public_key_authentication.md
+++ b/doc/public_key_authentication.md
@@ -25,24 +25,37 @@ To take advantage of PKA, the following is required:
Before using SCS3, it must be patched [scs3.patch.txt](https://github.com/polhenarejos/pico-hsm/files/8890050/scs3.patch.txt). See [SCS3](/doc/scs3.md "SCS3") for further details.
-### Generate the authentication key
+### Generate the authentication key
On a secondary device, generate a private key, on the ECC 256 bits (`brainpoolP256r1` or `secp192r1`). Label it with an easy name, such as "Authentication".
+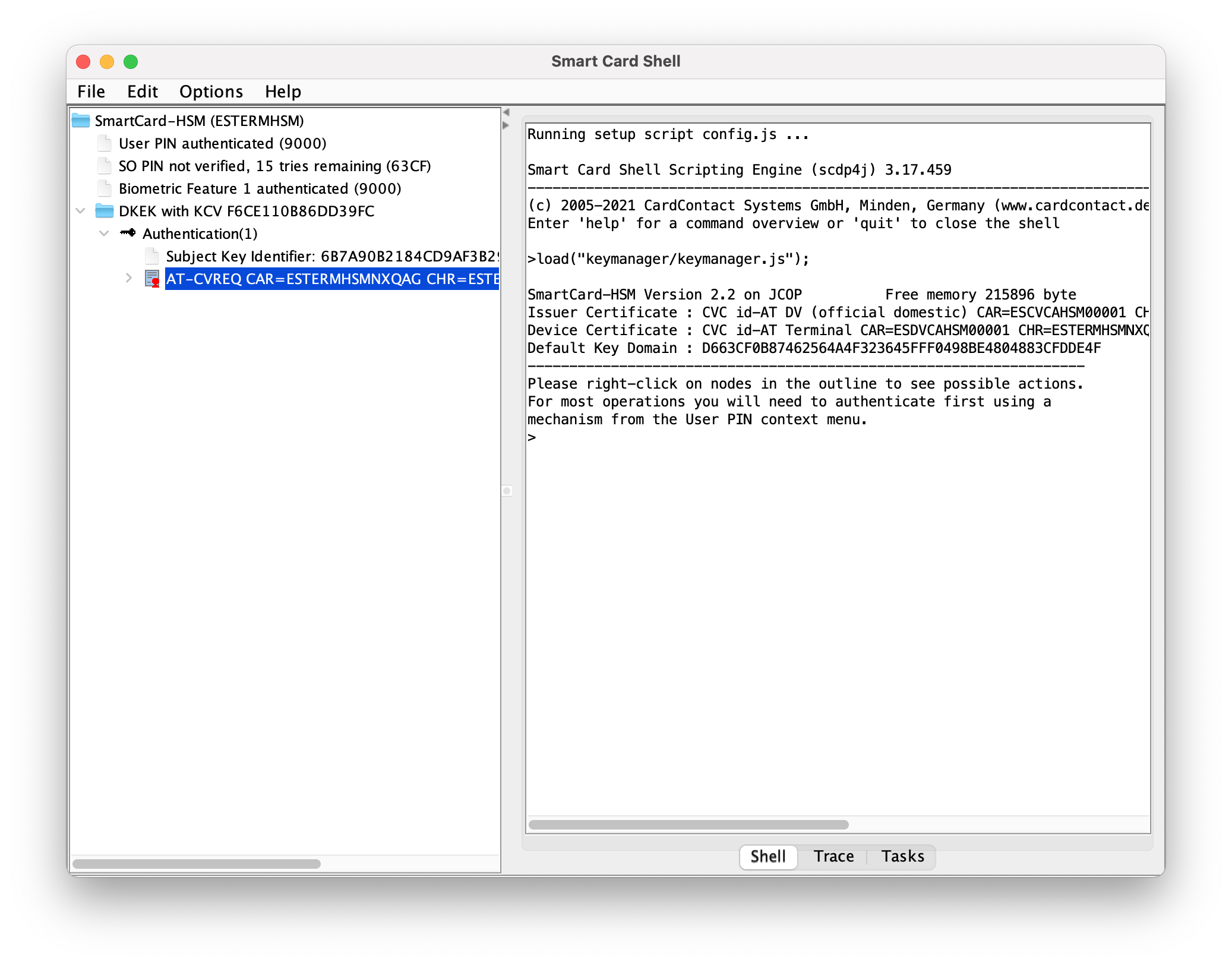 +
Once finished, export the public key.
+
+
Once finished, export the public key.
+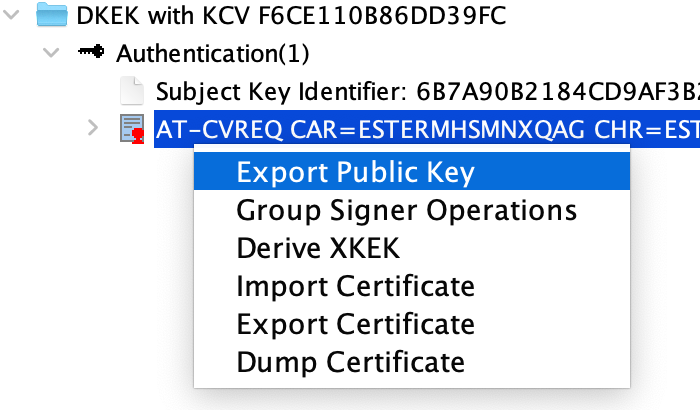 +
### Initialization
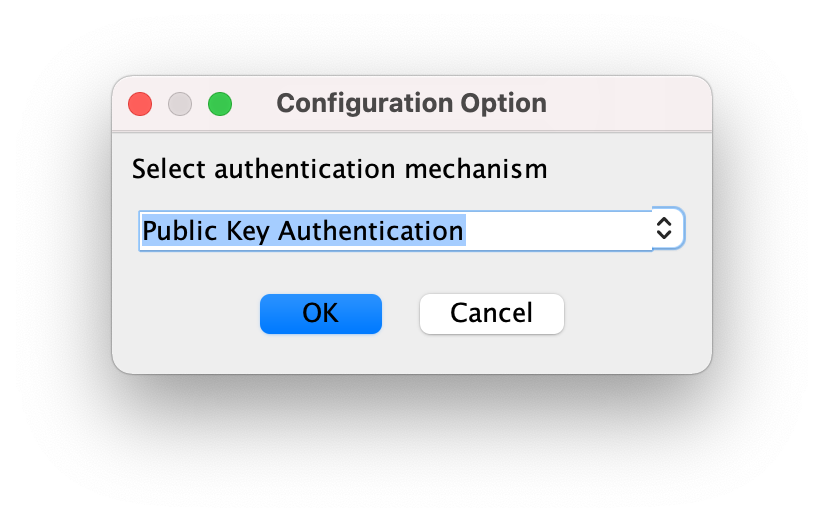
On the primary device, initialize it. When prompting for an authentication mechanism, select "Public Key Authentication".
+
+
### Initialization
On the primary device, initialize it. When prompting for an authentication mechanism, select "Public Key Authentication".
+
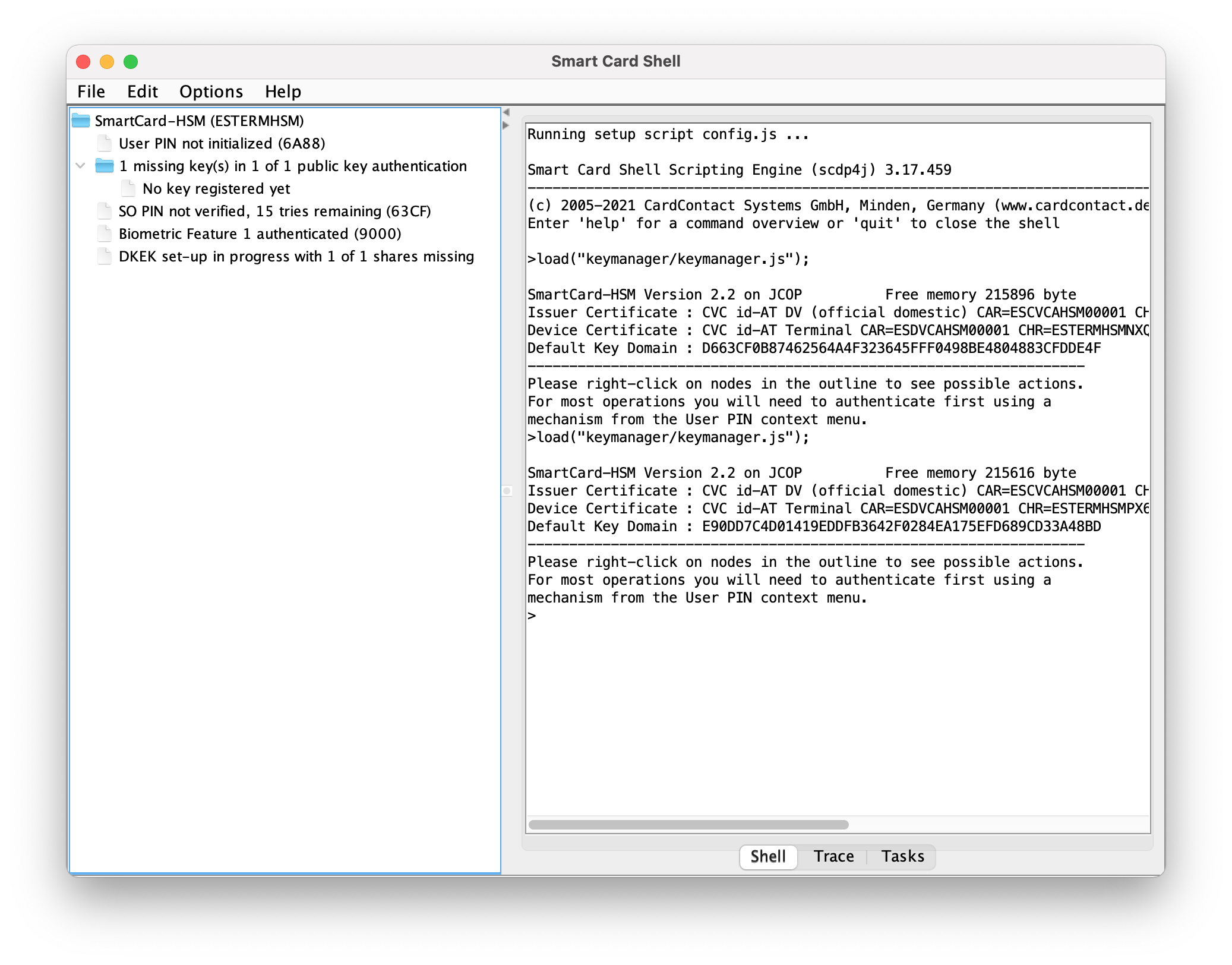 +
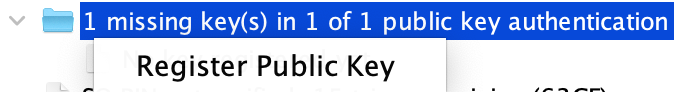
Once finished, register the exported public key. A message of `0 authenticated public key(s) in 1 of 1 scheme` will appear if it is properly registered.
-### Authentication
+
+
Once finished, register the exported public key. A message of `0 authenticated public key(s) in 1 of 1 scheme` will appear if it is properly registered.
-### Authentication
+
 -Plug the secondary device that stores the private key (do not load the device in the SCS3 tool).
+
+### Authentication
+
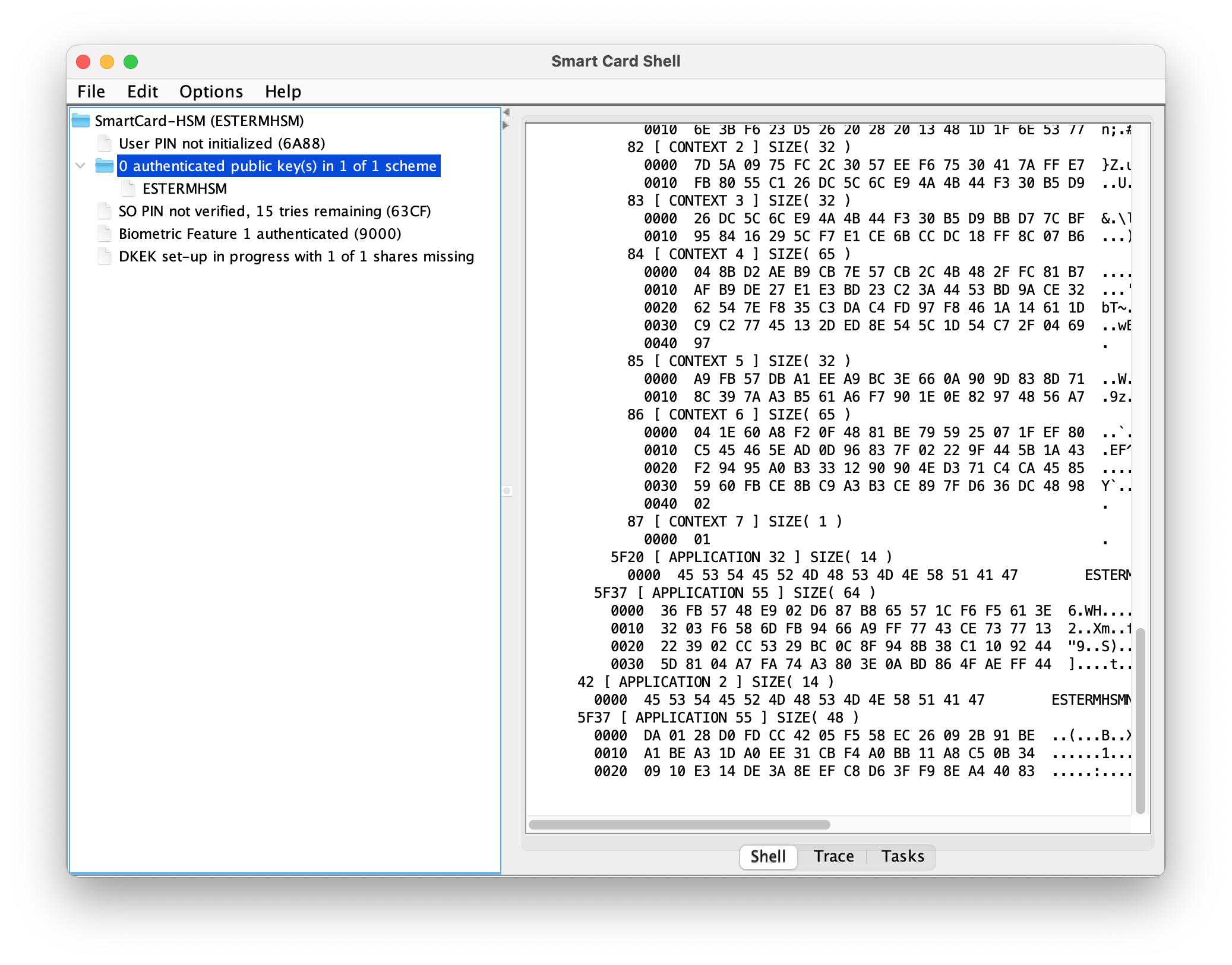
+Plug the secondary device that stores the private key (do not load the device in the SCS3 tool) and initiate the public key authentication.
+
+
-Plug the secondary device that stores the private key (do not load the device in the SCS3 tool).
+
+### Authentication
+
+Plug the secondary device that stores the private key (do not load the device in the SCS3 tool) and initiate the public key authentication.
+
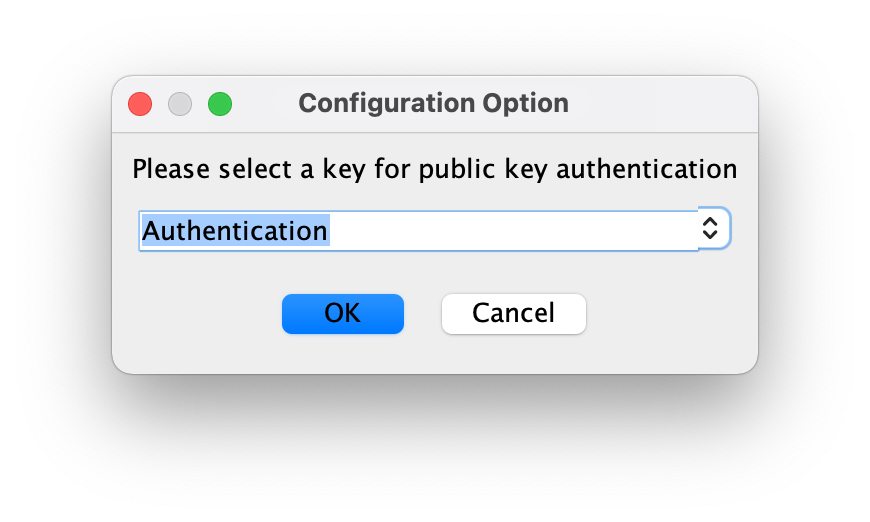
+ Select the secondary card and the Authentication private key (or the name you labeled it).
+
Select the secondary card and the Authentication private key (or the name you labeled it).
+ +
Introduce the PIN of the secondary device.
If the private key matches with the registered public key, the primary device will grant access and it will display `User PIN authenticated (9000)` (despite no PIN is provided).
+
Introduce the PIN of the secondary device.
If the private key matches with the registered public key, the primary device will grant access and it will display `User PIN authenticated (9000)` (despite no PIN is provided).
 +
Once finished, export the public key.
+
+
Once finished, export the public key.
+ +
### Initialization
On the primary device, initialize it. When prompting for an authentication mechanism, select "Public Key Authentication".
+
+
### Initialization
On the primary device, initialize it. When prompting for an authentication mechanism, select "Public Key Authentication".
+
 +
Once finished, register the exported public key. A message of `0 authenticated public key(s) in 1 of 1 scheme` will appear if it is properly registered.
-### Authentication
+
+
Once finished, register the exported public key. A message of `0 authenticated public key(s) in 1 of 1 scheme` will appear if it is properly registered.
-### Authentication
+
 -Plug the secondary device that stores the private key (do not load the device in the SCS3 tool).
+
+### Authentication
+
+Plug the secondary device that stores the private key (do not load the device in the SCS3 tool) and initiate the public key authentication.
+
+
-Plug the secondary device that stores the private key (do not load the device in the SCS3 tool).
+
+### Authentication
+
+Plug the secondary device that stores the private key (do not load the device in the SCS3 tool) and initiate the public key authentication.
+
+ Select the secondary card and the Authentication private key (or the name you labeled it).
+
Select the secondary card and the Authentication private key (or the name you labeled it).
+ +
Introduce the PIN of the secondary device.
If the private key matches with the registered public key, the primary device will grant access and it will display `User PIN authenticated (9000)` (despite no PIN is provided).
+
Introduce the PIN of the secondary device.
If the private key matches with the registered public key, the primary device will grant access and it will display `User PIN authenticated (9000)` (despite no PIN is provided).