diff --git a/CMakeLists.txt b/CMakeLists.txt
index 7ab5f3b..dbd7ce5 100644
--- a/CMakeLists.txt
+++ b/CMakeLists.txt
@@ -1,17 +1,17 @@
- #
+ #
# This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
# Copyright (c) 2022 Pol Henarejos.
- #
- # This program is free software: you can redistribute it and/or modify
- # it under the terms of the GNU General Public License as published by
+ #
+ # This program is free software: you can redistribute it and/or modify
+ # it under the terms of the GNU General Public License as published by
# the Free Software Foundation, version 3.
#
- # This program is distributed in the hope that it will be useful, but
- # WITHOUT ANY WARRANTY; without even the implied warranty of
- # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ # This program is distributed in the hope that it will be useful, but
+ # WITHOUT ANY WARRANTY; without even the implied warranty of
+ # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
# General Public License for more details.
#
- # You should have received a copy of the GNU General Public License
+ # You should have received a copy of the GNU General Public License
# along with this program. If not, see .
#
@@ -88,7 +88,7 @@ target_sources(pico_hsm PUBLIC
${CMAKE_CURRENT_LIST_DIR}/src/hsm/files.c
${CMAKE_CURRENT_LIST_DIR}/src/hsm/kek.c
${CMAKE_CURRENT_LIST_DIR}/src/hsm/oid.c
-
+
${CMAKE_CURRENT_LIST_DIR}/pico-ccid/mbedtls/library/aes.c
${CMAKE_CURRENT_LIST_DIR}/pico-ccid/mbedtls/library/asn1write.c
${CMAKE_CURRENT_LIST_DIR}/pico-ccid/mbedtls/library/bignum.c
diff --git a/README.md b/README.md
index 9bad70a..9cef6ac 100644
--- a/README.md
+++ b/README.md
@@ -86,7 +86,7 @@ This feature protects the user from unwanted uses from background applications t
It allows the storage of arbitrary files with binary data.
### Real time clock (RTC)
-Pico HSM has a RTC with external datetime setting and getting.
+Pico HSM has a RTC with external datetime setting and getting.
### Secure Messaging (secure channel)
Pico HSM supports secure channel, where the data packets between the host and device are encrypted to avoid man-in-the-middle attacks.
@@ -98,7 +98,7 @@ A specific session PIN can be set during the session opening to avoid the system
Secure channel messages are secured with a certificate issued by an external PKI.
### Multiple key domains
-Key domains are domains to store separate private/secret keys. Each domain is protected by a DKEK, independent from the other domains. Private/secret keys can be generated in different key domains to be used with separated DKEK.
+Key domains are domains to store separate private/secret keys. Each domain is protected by a DKEK, independent from the other domains. Private/secret keys can be generated in different key domains to be used with separated DKEK.
Therefore, a single device may contain different domains with independent keys.
### Key usage counter
@@ -113,17 +113,17 @@ In PKA, the PIN is used for protecting the DKEK, as classic method with only PIN
[^1]: PKCS11 modules (`pkcs11-tool` and `sc-tool`) do not support CMAC and key derivation. It must be processed through raw APDU command (`opensc-tool -s`).
[^2]: Available via SCS3 tool. See [SCS3](/doc/scs3.md "SCS3") for more information.
-[^3]: Imports are available only if the Pico HSM is previously initialized with a DKEK and the DKEK shares are available during the import process.
+[^3]: Imports are available only if the Pico HSM is previously initialized with a DKEK and the DKEK shares are available during the import process.
## Security considerations
-All secret keys (asymmetric and symmetric) are stored encrypted in the flash memory of the Raspberry Pico. DKEK is used as a 256 bit AES key to protect private and secret keys. Keys are never stored in RAM except for signature and decryption operations and only during the process. All keys (including DKEK) are loaded and cleared every time to avoid potential security flaws.
+All secret keys (asymmetric and symmetric) are stored encrypted in the flash memory of the Raspberry Pico. DKEK is used as a 256 bit AES key to protect private and secret keys. Keys are never stored in RAM except for signature and decryption operations and only during the process. All keys (including DKEK) are loaded and cleared every time to avoid potential security flaws.
At the same time, DKEK is encrypted with doubled salted and hashed PIN. Also, the PIN is hashed in memory during the session. Hence, PIN is never stored in plain text neither in flash nor in memory. Note that PIN is conveyed from the host to the HSM in plain text if no secure channel is provided.
If the Pico is stolen the contents of private and secret keys cannot be read without the PIN, even if the flash memory is dumped.
## Download
-Please, go to the Release page and download the UF2 file for your board.
+Please, go to the Release page and download the UF2 file for your board.
Note that UF2 files are shiped with a dummy VID/PID to avoid license issues (FEFF:FCFD). If you are planning to use it with OpenSC or similar, you should modify Info.plist of CCID driver to add these VID/PID or use the VID/PID patcher as follows:
`./patch_vidpid.sh VID:PID input_hsm_file.uf2 output_hsm_file.uf2`
@@ -179,7 +179,7 @@ For Public Key Authentication, check [doc/public_key_authentication.md](/doc/pub
## Operation time
### Keypair generation
-Generating EC keys is almost instant. RSA keypair generation takes some time, specially for `3072` and `4096` bits.
+Generating EC keys is almost instant. RSA keypair generation takes some time, specially for `3072` and `4096` bits.
| RSA key length (bits) | Average time (seconds) |
| :---: | :---: |
@@ -227,7 +227,7 @@ While processing, the Pico HSM is busy and cannot receive additional commands un
## Driver
-Pico HSM uses the `sc-hsm` driver provided by [OpenSC](https://github.com/OpenSC/OpenSC/ "OpenSC") or the `sc-hsm-embedded` driver provided by [CardContact](https://github.com/CardContact/sc-hsm-embedded "CardContact"). This driver utilizes the standardized PKCS#11 interface to communicate with the user and it can be used with many engines that accept PKCS#11 interface, such as OpenSSL, P11 library or pkcs11-tool.
+Pico HSM uses the `sc-hsm` driver provided by [OpenSC](https://github.com/OpenSC/OpenSC/ "OpenSC") or the `sc-hsm-embedded` driver provided by [CardContact](https://github.com/CardContact/sc-hsm-embedded "CardContact"). This driver utilizes the standardized PKCS#11 interface to communicate with the user and it can be used with many engines that accept PKCS#11 interface, such as OpenSSL, P11 library or pkcs11-tool.
Pico HSM relies on PKCS#15 structure to store and manipulate the internal files (PINs, private keys, certificates, etc.) and directories. Therefore, it accepts the commands from `pkcs15-tool`. For instance, `pkcs15-tool -D` will list all elements stored in the Pico HSM.
diff --git a/build_pico_hsm.sh b/build_pico_hsm.sh
index 25c154d..26cc14e 100755
--- a/build_pico_hsm.sh
+++ b/build_pico_hsm.sh
@@ -46,8 +46,8 @@ for board in adafruit_feather_rp2040 \
wiznet_w5100s_evb_pico
do
rm -rf *
- PICO_SDK_PATH=~/Devel/pico/pico-sdk cmake .. -DPICO_BOARD=$board
+ PICO_SDK_PATH=~/Devel/pico/pico-sdk cmake .. -DPICO_BOARD=$board
make -kj20
mv pico_hsm.uf2 ../release/pico_hsm_$board-$VERSION_MAJOR.$VERSION_MINOR.uf2
-
+
done
diff --git a/burn-cvcerts.py b/burn-cvcerts.py
index fe835be..8359e03 100644
--- a/burn-cvcerts.py
+++ b/burn-cvcerts.py
@@ -7,29 +7,31 @@ from cvc.asn1 import ASN1
import json
import urllib.request
import base64
-from getpass import getpass
from binascii import hexlify
+
class APDUResponse(Exception):
def __init__(self, sw1, sw2):
self.sw1 = sw1
self.sw2 = sw2
super().__init__(f'SW:{sw1:02X}{sw2:02X}')
-
+
+
def send_apdu(card, command, p1, p2, data):
- lc = [0x00] + list(len(data).to_bytes(2,'big'))
+ lc = [0x00] + list(len(data).to_bytes(2, 'big'))
le = [0x00, 0x00]
if (isinstance(command, list) and len(command) > 1):
apdu = command
else:
apdu = [0x00, command]
-
+
apdu = apdu + [p1, p2] + lc + data + le
response, sw1, sw2 = card.connection.transmit(apdu)
if (sw1 != 0x90):
- raise APDUResponse(sw1,sw2)
+ raise APDUResponse(sw1, sw2)
return response
+
def main():
print('Pico HSM burning certificates tool v1.0')
print('Author: Pol Henarejos')
@@ -40,7 +42,8 @@ def main():
print('* PLEASE READ IT CAREFULLY *')
print('********************************')
print('')
- print('This tool will erase and reset your device. It will delete all private and secret keys.')
+ print('This tool will erase and reset your device. It will delete all '
+ 'private and secret keys.')
print('Are you sure?')
_ = input('[Press enter to confirm]')
cardtype = AnyCardType()
@@ -48,47 +51,59 @@ def main():
# request card insertion
cardrequest = CardRequest(timeout=10, cardType=cardtype)
card = cardrequest.waitforcard()
-
+
# connect to the card and perform a few transmits
card.connection.connect()
-
- reset_data = [0x80, 0x02, 0x00, 0x01, 0x81, 0x06, 0x36, 0x34, 0x38, 0x32, 0x31, 0x39, 0x82, 0x08, 0x35, 0x37, 0x36, 0x32, 0x31, 0x38, 0x38, 0x30, 0x91, 0x01, 0x03]
+
+ reset_data = [0x80, 0x02, 0x00, 0x01, 0x81, 0x06, 0x36, 0x34, 0x38,
+ 0x32, 0x31,
+ 0x39, 0x82, 0x08, 0x35, 0x37, 0x36, 0x32, 0x31, 0x38,
+ 0x38, 0x30, 0x91, 0x01, 0x03]
response = send_apdu(card, [0x80, 0x50], 0x00, 0x00, reset_data)
-
- response = send_apdu(card, 0xB1, 0xCE, 0x00, [0x54,0x02,0x00,0x00])
-
+
+ response = send_apdu(card, 0xB1, 0xCE, 0x00, [0x54, 0x02, 0x00, 0x00])
+
cert = bytearray(response)
Y = CVC().decode(cert).pubkey().find(0x86).data()
print(f'Public Point: {hexlify(Y).decode()}')
-
- user_agent = 'Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.9.0.7) Gecko/2009021910 Firefox/3.0.7'
+
+ user_agent = 'Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; '
+ 'rv:1.9.0.7) Gecko/2009021910 Firefox/3.0.7'
pbk = base64.urlsafe_b64encode(Y)
- data = urllib.parse.urlencode({'pubkey':pbk}).encode()
- req = urllib.request.Request("https://www.henarejos.me/pico-hsm/cvc/", method='POST', data=data, headers={'User-Agent':user_agent,} ) #The assembled request
+ data = urllib.parse.urlencode({'pubkey': pbk}).encode()
+ req = urllib.request.Request("https://www.henarejos.me/pico-hsm/cvc/",
+ method='POST',
+ data=data,
+ headers={'User-Agent': user_agent, })
response = urllib.request.urlopen(req)
resp = response.read().decode('utf-8')
j = json.loads(resp)
print('Device name: '+j['devname'])
- dataef = base64.urlsafe_b64decode(j['cvcert']) + base64.urlsafe_b64decode(j['dvcert'])
-
- response = send_apdu(card, 0xa4, 0x00, 0x00, [0x2f,0x02])
+ dataef = base64.urlsafe_b64decode(
+ j['cvcert']) + base64.urlsafe_b64decode(j['dvcert'])
+
+ response = send_apdu(card, 0xa4, 0x00, 0x00, [0x2f, 0x02])
pin = b'648219'
response = send_apdu(card, 0x20, 0x00, 0x81, list(pin))
-
- apdu_data = [0x54, 0x02, 0x00, 0x00] + list(ASN1.make_tag(0x53, dataef))
+
+ apdu_data = [0x54, 0x02, 0x00, 0x00] + \
+ list(ASN1.make_tag(0x53, dataef))
response = send_apdu(card, 0xd7, 0x00, 0x00, apdu_data)
-
+
print('Certificate uploaded successfully!')
print('')
- print('Note that the device is initialized with a default PIN and configuration.')
- print('Now you can initialize the device as usual with you chosen PIN and configuration options.')
-
+ print('Note that the device is initialized with a default PIN and '
+ 'configuration.')
+ print('Now you can initialize the device as usual with you chosen PIN '
+ 'and configuration options.')
+
except CardRequestTimeoutException:
print('time-out: no card inserted during last 10s')
+
def run():
main()
+
if __name__ == "__main__":
run()
-
\ No newline at end of file
diff --git a/doc/aes.md b/doc/aes.md
index 3e0504b..75df01c 100644
--- a/doc/aes.md
+++ b/doc/aes.md
@@ -54,4 +54,4 @@ Using decrypt algorithm AES-CBC
This is a text.
```
-AES-CBC it is a block operation and it requires an input size multiple of 16 bytes. Thus, for a trivial data, a padding operation has to be performed beforehand.
+AES-CBC it is a block operation and it requires an input size multiple of 16 bytes. Thus, for a trivial data, a padding operation has to be performed beforehand.
diff --git a/doc/asymmetric-ciphering.md b/doc/asymmetric-ciphering.md
index c348717..8b87707 100644
--- a/doc/asymmetric-ciphering.md
+++ b/doc/asymmetric-ciphering.md
@@ -24,12 +24,12 @@ This algorithm uses the PKCSv1.5 padding. It is considered deprecated and insecu
First, we encrypt the data with the public key:
```
-$ openssl rsautl -encrypt -inkey 1.pub -in data -pubin -out data.crypt
+$ openssl rsautl -encrypt -inkey 1.pub -in data -pubin -out data.crypt
```
Then, we decrypt with the private key inside the Pico HSM:
-```
+```
$ pkcs11-tool --id 1 --pin 648219 --decrypt --mechanism RSA-PKCS -i data.crypt
Using slot 0 with a present token (0x0)
Using decrypt algorithm RSA-PKCS
@@ -54,7 +54,7 @@ $ openssl rsautl -encrypt -inkey 1.pub -in data_pad -pubin -out data.crypt -raw
Then, we decrypt with the private key inside the Pico HSM:
```
-$ cat data.crypt|pkcs11-tool --id 4 --pin 648219 --decrypt --mechanism RSA-X-509
+$ cat data.crypt|pkcs11-tool --id 4 --pin 648219 --decrypt --mechanism RSA-X-509
Using slot 0 with a present token (0x0)
Using decrypt algorithm RSA-X-509
This is a test string. Be safe, be secure.
@@ -78,7 +78,7 @@ This is a test string. Be safe, be secure.
```
## ECDH-DERIVE
-ECC keys do not allow ciphering operations. Instead, the ECDH scheme provides a mechanism to exchange a shared symmetric key without transmitting it to the remote part. The shared key is composed by multiplying the local private key and the remote public key.
+ECC keys do not allow ciphering operations. Instead, the ECDH scheme provides a mechanism to exchange a shared symmetric key without transmitting it to the remote part. The shared key is composed by multiplying the local private key and the remote public key.
First, we create the remote part, Bob, by generating an ECC keypair and getting the public key:
```
@@ -104,8 +104,8 @@ No output is displayed if both are equal.
You can also view the contents of both keys:
```
-$ xxd -p bob-mine.der
+$ xxd -p bob-mine.der
9874558aefa9d92cc051e5da6d1753987e5314925d6d78bf
-$ xxd -p mine-bob.der
+$ xxd -p mine-bob.der
9874558aefa9d92cc051e5da6d1753987e5314925d6d78bf
```
diff --git a/doc/backup-and-restore.md b/doc/backup-and-restore.md
index 4a5bb1b..b7c078b 100644
--- a/doc/backup-and-restore.md
+++ b/doc/backup-and-restore.md
@@ -29,15 +29,15 @@ symbols.
Please keep the generated DKEK share file in a safe location. We also recommend to keep a
paper printout, in case the electronic version becomes unavailable. A printable version
of the file can be generated using "openssl base64 -in ".
-Enter password to encrypt DKEK share :
+Enter password to encrypt DKEK share :
-Please retype password to confirm :
+Please retype password to confirm :
Enciphering DKEK share, please wait...
DKEK share created and saved to dkek.pbe
```
-The generated file `dkek.pbe` contains the DKEK. Technically, it contains a share. But if a device is initialized with one share, it is equivalent to contain the full DKEK.
+The generated file `dkek.pbe` contains the DKEK. Technically, it contains a share. But if a device is initialized with one share, it is equivalent to contain the full DKEK.
Keep these file in a safe place. If this file is lost, you can export the private keys but you will not be able to import into another device or in the same device if it is initialized again.
@@ -52,7 +52,7 @@ At this moment, the Pico HSM expects the DKEK. It is loaded with the following c
```
$ sc-hsm-tool --import-dkek-share dkek.pbe
Using reader with a card: Free Software Initiative of Japan Gnuk
-Enter password to decrypt DKEK share :
+Enter password to decrypt DKEK share :
Deciphering DKEK share, please wait...
DKEK share imported
@@ -81,7 +81,7 @@ And finally, all are imported one after the other, without special order:
```
$ sc-hsm-tool --import-dkek-share dkek-share-1.pbe
Using reader with a card: Free Software Initiative of Japan Gnuk
-Enter password to decrypt DKEK share :
+Enter password to decrypt DKEK share :
Deciphering DKEK share, please wait...
DKEK share imported
@@ -90,7 +90,7 @@ DKEK import pending, 2 share(s) still missing
$ sc-hsm-tool --import-dkek-share dkek-share-2.pbe
Using reader with a card: Free Software Initiative of Japan Gnuk
-Enter password to decrypt DKEK share :
+Enter password to decrypt DKEK share :
Deciphering DKEK share, please wait...
DKEK share imported
@@ -99,7 +99,7 @@ DKEK import pending, 1 share(s) still missing
$ sc-hsm-tool --import-dkek-share dkek-share-1.pbe
Using reader with a card: Free Software Initiative of Japan Gnuk
-Enter password to decrypt DKEK share :
+Enter password to decrypt DKEK share :
Deciphering DKEK share, please wait...
DKEK share imported
@@ -110,7 +110,7 @@ DKEK key check value : 4B7DA256ACD4EF62
### DKEK n-of-m threshold scheme
This scheme provides an extra level of flexiblity, as not all custodians are necessary to import the DKEK share. For instance, with the previous schemes, if a custodian gets unavailable, the initialization will block until the missing custodian can got to finalize the initialization.
-With n-of-m threshold scheme, it flexibilizes the number of required custodians to reduce failure points. If a share is lost, the DKEK can still be recovered without major implications.
+With n-of-m threshold scheme, it flexibilizes the number of required custodians to reduce failure points. If a share is lost, the DKEK can still be recovered without major implications.
This scheme is not a replacement of DKEK shares. Instead, it splits the DKEK share encryption password amongst the n-of-m threshold scheme. For instance, if you define 2 shares and a scheme of 3-of-5 threshold for each share, it will imply 10 different custodians, where 6 are necessary to load both shares. You can also mix one share with traditional passphrase and the other with the n-of-m threshold scheme.
@@ -123,7 +123,7 @@ Using reader with a card:Free Software Initiative of Japan Gnuk
The DKEK will be enciphered using a randomly generated 64 bit password.
This password is split using a (3-of-5) threshold scheme.
-Please keep the generated and encrypted DKEK file in a safe location. We also recommend
+Please keep the generated and encrypted DKEK file in a safe location. We also recommend
to keep a paper printout, in case the electronic version becomes unavailable. A printable version
of the file can be generated using "openssl base64 -in ".
@@ -191,7 +191,7 @@ Private RSA Key [Certificate]
...
```
-Note that `Key ref` and `ID` may be different. Whilst different keys may share the same `ID` (highly discouraged), the `Key ref` is a value internally computed and unique.
+Note that `Key ref` and `ID` may be different. Whilst different keys may share the same `ID` (highly discouraged), the `Key ref` is a value internally computed and unique.
To export and wrap the private key:
@@ -199,10 +199,10 @@ To export and wrap the private key:
$ sc-hsm-tool --wrap-key wrap-key.bin --key-reference 1 --pin 648219
```
-A file named `wrap-key.bin` is created with the private key encrypted securely with the DKEK.
+A file named `wrap-key.bin` is created with the private key encrypted securely with the DKEK.
## Restore
-To restore the wraped key, a device initialized with the same DKEK is mandatory.
+To restore the wraped key, a device initialized with the same DKEK is mandatory.
To unwrap the key:
diff --git a/doc/extra_command.md b/doc/extra_command.md
index fa5c086..38a3750 100644
--- a/doc/extra_command.md
+++ b/doc/extra_command.md
@@ -1,6 +1,6 @@
# Extra command
-Pico HSM supports a customized extra command to use with different options. Since the drivers in the market do not support the following features, a raw APDU command shall be sent.
+Pico HSM supports a customized extra command to use with different options. Since the drivers in the market do not support the following features, a raw APDU command shall be sent.
To send a raw APDU command, `opensc-tool -s ` can be used. The `APDU` parameter is a string of hexadecimal numbers and it takes the following form:
```
@@ -27,7 +27,7 @@ For example, to obtain the current datetime:
```
$ opensc-tool -s 80640A0008
Using reader with a card: Free Software Initiative of Japan Gnuk
-Sending: 80 64 0A 00 08
+Sending: 80 64 0A 00 08
Received (SW1=0x90, SW2=0x00):
07 E6 04 06 03 13 29 1E ......).
```
@@ -49,7 +49,7 @@ To set the reference datetime, a datetime string must be provided. For example:
```
$ opensc-tool -s 80640A000807E6040603132917
Using reader with a card: Free Software Initiative of Japan Gnuk
-Sending: 80 64 0A 00 08 07 E6 04 06 03 13 29 17
+Sending: 80 64 0A 00 08 07 E6 04 06 03 13 29 17
Received (SW1=0x90, SW2=0x00)
```
@@ -72,7 +72,7 @@ This feature is disabled by default but can be enabled rapidly by setting the LS
```
$ opensc-tool -s 806406000101
Using reader with a card: Free Software Initiative of Japan Gnuk
-Sending: 80 64 06 00 01 01
+Sending: 80 64 06 00 01 01
Received (SW1=0x90, SW2=0x00)
```
@@ -99,7 +99,7 @@ This feature is disabled by default but can be enabled rapidly by setting the 2n
```
$ opensc-tool -s 806406000102
Using reader with a card: Free Software Initiative of Japan Gnuk
-Sending: 80 64 06 00 01 01
+Sending: 80 64 06 00 01 01
Received (SW1=0x90, SW2=0x00)
```
diff --git a/doc/public_key_authentication.md b/doc/public_key_authentication.md
index 711918f..b4a50cb 100644
--- a/doc/public_key_authentication.md
+++ b/doc/public_key_authentication.md
@@ -29,7 +29,7 @@ On a secondary device, generate a private key, on the ECC 256 bits (`brainpoolP2
 -Once finished, export the public key.
+Once finished, export the public key.
-Once finished, export the public key.
+Once finished, export the public key.
 @@ -64,17 +64,17 @@ From now on, you have full access and can operate normally with the primary devi
Pico HSM uses the PIN to protect the DKEK, which is lately used to protect private/secret keys and wrap/unwrap. However, when PKA is enabled, the authentication is not performed by introducing any PIN.
Authenticated privileges are granted when PKA succeeds, regardless of PIN, which is optional.
-Nevertheless, **it is extremely recommended to combine PKA with PIN**. Note that when combined, only PKA grants authenticated privileges. Therefore, if both schemes are setup, it is necessary to unlock the DKEK with PIN verification.
+Nevertheless, **it is extremely recommended to combine PKA with PIN**. Note that when combined, only PKA grants authenticated privileges. Therefore, if both schemes are setup, it is necessary to unlock the DKEK with PIN verification.
Otherwise, it will not be possible to operate with private/secret keys despite the user will be logged in.
With this scheme, multiple custodians may authenticate the device individually and remotely and, when fully authenticated, the master user can unlock the DKEK with the PIN.
-Moreover, with this approach the device is kept safe and neither the DKEK nor the private/secret keys are stored in plain text in the device.
+Moreover, with this approach the device is kept safe and neither the DKEK nor the private/secret keys are stored in plain text in the device.
Even though the flash memory is dumped by an attacker, it will not be possible to decipher any sensitive data or key.
Initialization of the device with PKA **and** PIN can be achieved with SCS3 or OpenSC:
-**Note:** do not import any DKEK share or DKEK operation before PKA and PIN setup.
+**Note:** do not import any DKEK share or DKEK operation before PKA and PIN setup.
### With OpenSC
@@ -84,9 +84,9 @@ Use the following command (or similar), which accepts the use of PIN parameter *
sc-hsm-tool -X --so-pin 1234567890123456 --pin 648219 -K 1 -n 1 -s 1
```
-and PKA and PIN are enabled, jointly with DKEK protection.
+and PKA and PIN are enabled, jointly with DKEK protection.
-### With SCS3
+###�With SCS3
Unfortunately, SCS3 does not allow to initialize the device with PKA and PIN at the same time, though it can be achieved in separated steps:
@@ -94,4 +94,4 @@ Unfortunately, SCS3 does not allow to initialize the device with PKA and PIN at
2. There is NO default PIN. So, DO NOT attempt to log in yet. A reset PIN shall be requested.
3. Click on ``Reset User-PIN``, introduce the SO-PIN configured during the initialization and introduce the desired User-PIN.
-When done, the device will be configured with PIN **and** PKA.
+When done, the device will be configured with PIN **and** PKA.
diff --git a/doc/scs3.md b/doc/scs3.md
index 92573e1..8dd9dbe 100644
--- a/doc/scs3.md
+++ b/doc/scs3.md
@@ -4,11 +4,11 @@ SCS3 tool is a specific tool developed by CardContact to manage HSM. Thanks to i
- Import PKCS12 private keys and certificates.
- Import private keys and certificates from other Pico HSM devices in WKY format.
--
+-
Unfortunately, there is no pkcs11 tool or equivalent capable to perform the import. Since it uses the SC-HSM driver, it also supports the communication with the [SCS3 tool](https://www.openscdp.org/scsh3/ "SCS3 tool"). It can be downloaded from [here](https://www.openscdp.org/scsh3/download.html "here").
-However, SCS3 only works with those HSM manufactured by CardContact. The check is performed by means of trust store against the manufacturing certificates. For obvious reasons, these certificates can only be signed with the private keys of the Certificate Authorities listed in the trust store.
+However, SCS3 only works with those HSM manufactured by CardContact. The check is performed by means of trust store against the manufacturing certificates. For obvious reasons, these certificates can only be signed with the private keys of the Certificate Authorities listed in the trust store.
Pico HSM is shipped with its own CA certificates. To load this certificate onto the trust store of SCS3, the following line has to be appended to `SmartCardHSM.rootCerts` variable, near line `235` in the file `scs3/scsh/sc-hsm/SmartCardHSM.js`.
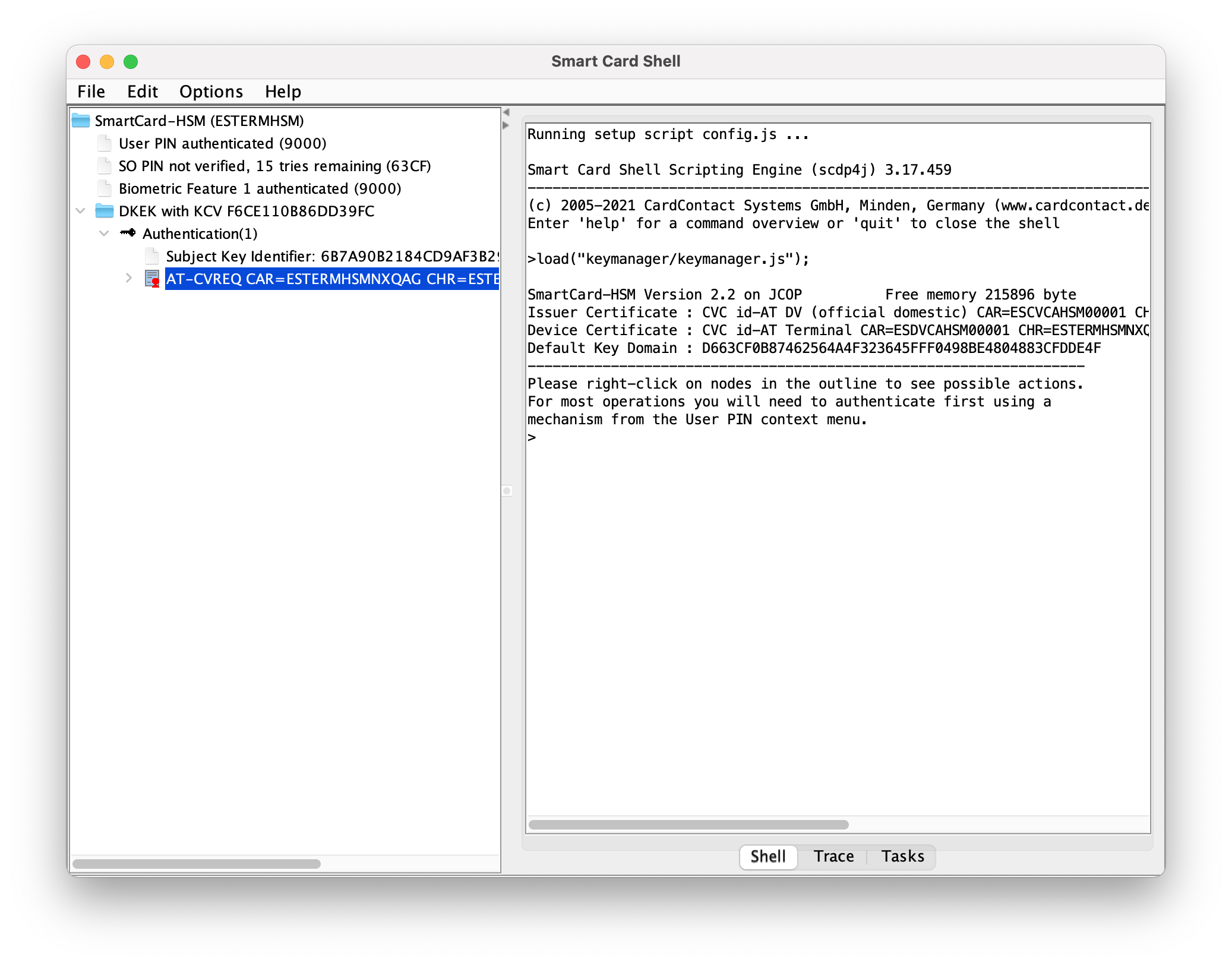
@@ -39,8 +39,8 @@ After this ammendment, the program can be started and the KeyManager can be invo
>load("keymanager/keymanager.js");
SmartCard-HSM Version 1.6 on JCOP Free memory 217104 byte
-Issuer Certificate : CVC id-AT DV (official domestic) CAR=ESCVCAHSM00001 CHR=ESDVCAHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2025
-Device Certificate : CVC id-AT Terminal CAR=ESDVCAHSM00001 CHR=ESTERMHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2023
+Issuer Certificate : CVC id-AT DV (official domestic) CAR=ESCVCAHSM00001 CHR=ESDVCAHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2025
+Device Certificate : CVC id-AT Terminal CAR=ESDVCAHSM00001 CHR=ESTERMHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2023
Default Key Domain : 0F89B400975EDD2D425ABF85F2FBD318779B3D85475E65D4
-------------------------------------------------------------------
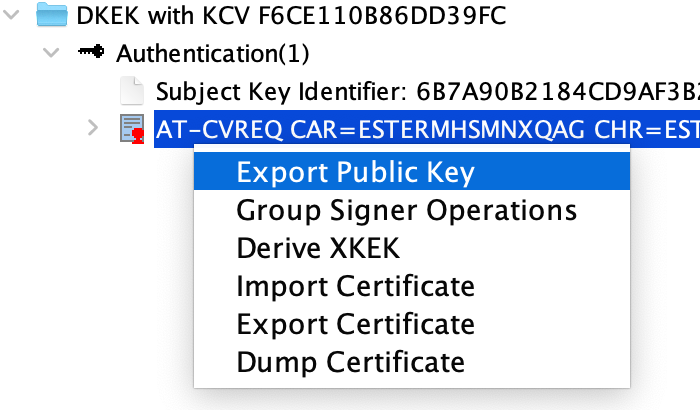
Please right-click on nodes in the outline to see possible actions.
@@ -60,7 +60,7 @@ It can be executed in a Terminal via
```
## DKEK requirement
-In order to perform the import, private keys must be wrapped with the same DKEK present in the Pico HSM. Thus, the Pico HSM must be previously initialized with at minimum of 1 DKEK share. This share will be used to wrap the private key before import.
+In order to perform the import, private keys must be wrapped with the same DKEK present in the Pico HSM. Thus, the Pico HSM must be previously initialized with at minimum of 1 DKEK share. This share will be used to wrap the private key before import.
Note that the DKEK share shall be available before the import. In this way, all custodians must be present during the import process, since they will have to introduce their respective DKEK.
diff --git a/doc/sign-verify.md b/doc/sign-verify.md
index 1c668e7..c7c1c93 100644
--- a/doc/sign-verify.md
+++ b/doc/sign-verify.md
@@ -1,7 +1,7 @@
# Sign and verify
Pico HSM supports in place signature of arbitrary data. It supports the following algorithms:
-* RSA-PKCS
+* RSA-PKCS
* RSA-X-509
* SHA1-RSA-PKCS
* SHA256-RSA-PKCS
@@ -32,7 +32,7 @@ $ openssl rsa -inform DER -outform PEM -in 1.der -pubin > 1.pub
At this moment, you are able to verify with the public key in `1.pub`. The signature is computed inside the Pico HSM with the private key. It never leaves the device.
## RSA-PKCS
-This algorithm is used to sign raw data.
+This algorithm is used to sign raw data.
To sign the data:
```
@@ -91,7 +91,7 @@ This algorithm uses the RSA-PKCS with PSS salt to randomize the signature. Pico
To sign the data:
```
$ pkcs11-tool --id 1 --sign --pin 648219 --mechanism RSA-PKCS-PSS -i data.sha1 -o data.sig
-```
+```
To verify the signature:
```
@@ -105,7 +105,7 @@ This algorithm takes the file as the input and sends its hash for signing with t
To sign the data:
```
$ pkcs11-tool --id 1 --sign --pin 648219 --mechanism SHA1-RSA-PKCS-PSS -i data -o data.sig
-```
+```
To verify the signature:
```
@@ -118,14 +118,14 @@ This is a raw ECDSA signature, which is usually used to sign a hashed message. `
To sign the data:
```
-$ pkcs11-tool --id 11 --sign --pin 648219 --mechanism ECDSA -i data.sha1 -o data.sig --signature-format openssl
+$ pkcs11-tool --id 11 --sign --pin 648219 --mechanism ECDSA -i data.sha1 -o data.sig --signature-format openssl
Using slot 0 with a present token (0x0)
Using signature algorithm ECDSA
```
To verify the signature:
```
-$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
+$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
Signature Verified Successfully
```
@@ -143,6 +143,6 @@ Using signature algorithm ECDSA-SHA256
The signature is verified with the hash:
```
-$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
+$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
Signature Verified Successfully
```
diff --git a/doc/store_data.md b/doc/store_data.md
index 66b1d21..eb5a8f9 100644
--- a/doc/store_data.md
+++ b/doc/store_data.md
@@ -9,7 +9,7 @@ Before writting a file into the Pico HSM, we generate the data file with the fol
```
$ echo 'Pico HSM is awesome!' > test
-```
+```
Then, we can store the data file with the following command:
@@ -43,7 +43,7 @@ Always provide a unique `--label`, as it will be used to index and reference the
To view the stored file, we can use the following command with the same label we employed:
```
-$ pkcs11-tool --read-object --type data --label 'test1'
+$ pkcs11-tool --read-object --type data --label 'test1'
Using slot 0 with a present token (0x0)
Pico HSM is awesome!
```
@@ -98,7 +98,7 @@ Data object 'test1'
applicationName: test1
Path: e82b0601040181c31f0201::cf00
Data (21 bytes): 5069636F2048534D20697320617765736F6D65210A
-
+
Data object 'test2'
applicationName: test2
Path: e82b0601040181c31f0201::cd01
diff --git a/doc/usage.md b/doc/usage.md
index e06e776..a4d65e4 100644
--- a/doc/usage.md
+++ b/doc/usage.md
@@ -1,7 +1,7 @@
# Usage
## Tools
-We use multiple tools and PKCS#11 drivers and modules, depending on the purpose.
+We use multiple tools and PKCS#11 drivers and modules, depending on the purpose.
* **pkcs11-tool**: from OpenSC. It interfaces with the HSM via PKCS#11 interface. It supports different drivers and modules.
* **sc-tool**: an alias of pkcs11-tool with the sc-hsm-embedded module. It is mainly used for AES management and it is defined as:
```
@@ -32,10 +32,10 @@ The first step is to initialize the HSM:
```
$ sc-hsm-tool --initialize --so-pin 3537363231383830 --pin 648219
```
-The PIN number is used to manage all private keys in the device. It supports three attemps. After the third PIN failure, it gets blocked.
+The PIN number is used to manage all private keys in the device. It supports three attemps. After the third PIN failure, it gets blocked.
The PIN accepts from 6 to 16 characters.
-The SO-PIN is used to unblock the PIN. It accepts 15 attemps. After 15 failed attempts, the device will be completely blocked and will be necessary to initialize again, erasing all private keys and losing the access. Therefore, keep the SO-PIN in a safe place.
+The SO-PIN is used to unblock the PIN. It accepts 15 attemps. After 15 failed attempts, the device will be completely blocked and will be necessary to initialize again, erasing all private keys and losing the access. Therefore, keep the SO-PIN in a safe place.
The SO-PIN is always 16 hexadecimal characters.
## PIN and SO-PIN management
@@ -62,7 +62,7 @@ To generate a RSA 2048 bits, use the following command:
$ pkcs11-tool -l --pin 648219 --keypairgen --key-type rsa:2048 --id 1 --label "RSA2K"
Using slot 0 with a present token (0x0)
Key pair generated:
-Private Key Object; RSA
+Private Key Object; RSA
label: RSA2K
ID: 1
Usage: decrypt, sign
@@ -77,7 +77,7 @@ The ID parameter is an internal hexadecimal number for easy identification. The
Pico HSM accepts RSA of 1024 (`rsa:1024`), 2048 (`rsa:2048`) and 4096 bits (`rsa:4096`).
-**Caution**: RSA 2048 bits may take more than 20 seconds. RSA 4096 bits may take more than 20 minutes. The Pico HSM will work as normally and neither the HSM nor the host will block. But, in the meantime, the Pico HSM will not accept any command.
+**Caution**: RSA 2048 bits may take more than 20 seconds. RSA 4096 bits may take more than 20 minutes. The Pico HSM will work as normally and neither the HSM nor the host will block. But, in the meantime, the Pico HSM will not accept any command.
An alternative is to generate the private key locally and import it to the HSM. This approach, however, is less secure as it does not use a True RNG or HRNG like Pico HSM. Use this approach if you have plugged a TRNG or you are not worried about obtaining the highest entropy.
Pico HSM also accepts ECDSA keypairs:
@@ -157,9 +157,9 @@ Certificate:
a0:30:b2:ec:d3:d6:0d:58:f3
Exponent: 65537 (0x10001)
X509v3 extensions:
- X509v3 Subject Key Identifier:
+ X509v3 Subject Key Identifier:
98:07:DA:13:B0:8E:A0:5C:97:83:68:FE:4A:25:8D:50:C4:DC:16:FA
- X509v3 Authority Key Identifier:
+ X509v3 Authority Key Identifier:
keyid:98:07:DA:13:B0:8E:A0:5C:97:83:68:FE:4A:25:8D:50:C4:DC:16:FA
X509v3 Basic Constraints: critical
@@ -173,7 +173,7 @@ Certificate:
99:2b:b2:82:66:c1:06:a7:2c:62:af:e2:e4:93:42:36:66:8d:
c5:3f:e1:ec:5f:9a:f8:5f:b3:6a:8f:0e:12:5d:c9:46:38:ea:
0b:08
-```
+```
The resulting file `cert.pem` contains the signed certificate in PEM format. Convert it into DER format and load it into the Pico HSM:
diff --git a/patch_vidpid.sh b/patch_vidpid.sh
index 0ec3ffb..ea47f29 100755
--- a/patch_vidpid.sh
+++ b/patch_vidpid.sh
@@ -1,19 +1,19 @@
#!/bin/bash
-#
+#
# This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
# Copyright (c) 2022 Pol Henarejos.
-#
-# This program is free software: you can redistribute it and/or modify
-# it under the terms of the GNU General Public License as published by
+#
+# This program is free software: you can redistribute it and/or modify
+# it under the terms of the GNU General Public License as published by
# the Free Software Foundation, version 3.
#
-# This program is distributed in the hope that it will be useful, but
-# WITHOUT ANY WARRANTY; without even the implied warranty of
-# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+# This program is distributed in the hope that it will be useful, but
+# WITHOUT ANY WARRANTY; without even the implied warranty of
+# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
# General Public License for more details.
#
-# You should have received a copy of the GNU General Public License
+# You should have received a copy of the GNU General Public License
# along with this program. If not, see .
#
diff --git a/src/hsm/cmd_challenge.c b/src/hsm/cmd_challenge.c
index 6f746b5..1fa5215 100644
--- a/src/hsm/cmd_challenge.c
+++ b/src/hsm/cmd_challenge.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/cmd_change_pin.c b/src/hsm/cmd_change_pin.c
index 874fc1e..ab57d92 100644
--- a/src/hsm/cmd_change_pin.c
+++ b/src/hsm/cmd_change_pin.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "crypto_utils.h"
#include "sc_hsm.h"
#include "kek.h"
diff --git a/src/hsm/cmd_cipher_sym.c b/src/hsm/cmd_cipher_sym.c
index 4ae4dd3..2fa7099 100644
--- a/src/hsm/cmd_cipher_sym.c
+++ b/src/hsm/cmd_cipher_sym.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/cmd_decrypt_asym.c b/src/hsm/cmd_decrypt_asym.c
index af6e0dc..147355e 100644
--- a/src/hsm/cmd_decrypt_asym.c
+++ b/src/hsm/cmd_decrypt_asym.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "common.h"
#include "mbedtls/ecdh.h"
#include "crypto_utils.h"
diff --git a/src/hsm/cmd_delete_file.c b/src/hsm/cmd_delete_file.c
index 6dd649d..3b69e78 100644
--- a/src/hsm/cmd_delete_file.c
+++ b/src/hsm/cmd_delete_file.c
@@ -1,27 +1,27 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
int cmd_delete_file() {
file_t *ef = NULL;
if (!isUserAuthenticated)
return SW_SECURITY_STATUS_NOT_SATISFIED();
-
+
if (apdu.nc == 0) {
ef = currentEF;
if (!(ef = search_dynamic_file(ef->fid)))
diff --git a/src/hsm/cmd_derive_asym.c b/src/hsm/cmd_derive_asym.c
index 907a2ec..00a8303 100644
--- a/src/hsm/cmd_derive_asym.c
+++ b/src/hsm/cmd_derive_asym.c
@@ -1,22 +1,22 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
#include "common.h"
-#include "mbedtls/ecdsa.h"
+#include "mbedtls/ecdsa.h"
#include "crypto_utils.h"
#include "sc_hsm.h"
@@ -43,7 +43,7 @@ int cmd_derive_asym() {
file_t *fkey;
if (!isUserAuthenticated)
return SW_SECURITY_STATUS_NOT_SATISFIED();
- if (!(fkey = search_dynamic_file((KEY_PREFIX << 8) | key_id)) || !fkey->data || file_get_size(fkey) == 0)
+ if (!(fkey = search_dynamic_file((KEY_PREFIX << 8) | key_id)) || !fkey->data || file_get_size(fkey) == 0)
return SW_FILE_NOT_FOUND();
if (key_has_purpose(fkey, ALGO_EC_DERIVE) == false)
return SW_CONDITIONS_NOT_SATISFIED();
@@ -52,7 +52,7 @@ int cmd_derive_asym() {
if (apdu.data[0] == ALGO_EC_DERIVE) {
mbedtls_ecdsa_context ctx;
mbedtls_ecdsa_init(&ctx);
-
+
int r;
r = load_private_key_ecdsa(&ctx, fkey);
if (r != CCID_OK) {
@@ -96,7 +96,7 @@ int cmd_derive_asym() {
mbedtls_mpi_free(&a);
mbedtls_mpi_free(&nd);
}
- else
+ else
return SW_WRONG_DATA();
return SW_OK();
}
diff --git a/src/hsm/cmd_external_authenticate.c b/src/hsm/cmd_external_authenticate.c
index 6ebfc73..df974e9 100644
--- a/src/hsm/cmd_external_authenticate.c
+++ b/src/hsm/cmd_external_authenticate.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/cmd_extras.c b/src/hsm/cmd_extras.c
index 5c1968f..440ed9b 100644
--- a/src/hsm/cmd_extras.c
+++ b/src/hsm/cmd_extras.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
#include "hardware/rtc.h"
#include "files.h"
diff --git a/src/hsm/cmd_general_authenticate.c b/src/hsm/cmd_general_authenticate.c
index 28bb876..26afc76 100644
--- a/src/hsm/cmd_general_authenticate.c
+++ b/src/hsm/cmd_general_authenticate.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -32,7 +32,7 @@ int cmd_general_authenticate() {
const uint8_t *pubkey = NULL;
uint16_t tag = 0x0;
uint8_t *tag_data = NULL, *p = NULL;
- size_t tag_len = 0;
+ size_t tag_len = 0;
while (walk_tlv(apdu.data+2, apdu.nc-2, &p, &tag, &tag_len, &tag_data)) {
if (tag == 0x80) {
pubkey = tag_data-1; //mbedtls ecdh starts reading one pos before
@@ -78,14 +78,14 @@ int cmd_general_authenticate() {
}
sm_derive_all_keys(derived, olen);
-
+
uint8_t *t = (uint8_t *)calloc(1, pubkey_len+16);
memcpy(t, "\x7F\x49\x3F\x06\x0A", 5);
if (sm_get_protocol() == MSE_AES)
memcpy(t+5, OID_ID_CA_ECDH_AES_CBC_CMAC_128, 10);
t[15] = 0x86;
memcpy(t+16, pubkey, pubkey_len);
-
+
res_APDU[res_APDU_size++] = 0x7C;
res_APDU[res_APDU_size++] = 20;
res_APDU[res_APDU_size++] = 0x81;
@@ -94,11 +94,11 @@ int cmd_general_authenticate() {
res_APDU_size += 8;
res_APDU[res_APDU_size++] = 0x82;
res_APDU[res_APDU_size++] = 8;
-
+
r = sm_sign(t, pubkey_len+16, res_APDU+res_APDU_size);
-
+
free(t);
- if (r != CCID_OK)
+ if (r != CCID_OK)
return SW_EXEC_ERROR();
res_APDU_size += 8;
}
diff --git a/src/hsm/cmd_initialize.c b/src/hsm/cmd_initialize.c
index 2a3a0de..86b4493 100644
--- a/src/hsm/cmd_initialize.c
+++ b/src/hsm/cmd_initialize.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -41,7 +41,7 @@ int cmd_initialize() {
has_session_pin = has_session_sopin = false;
uint16_t tag = 0x0;
uint8_t *tag_data = NULL, *p = NULL, *kds = NULL, *dkeks = NULL;
- size_t tag_len = 0;
+ size_t tag_len = 0;
while (walk_tlv(apdu.data, apdu.nc, &p, &tag, &tag_len, &tag_data)) {
if (tag == 0x80) { //options
file_t *tf = search_by_fid(EF_DEVOPS, NULL, SPECIFY_EF);
@@ -170,12 +170,12 @@ int cmd_initialize() {
return SW_EXEC_ERROR();
}
mbedtls_ecdsa_free(&ecdsa);
-
+
file_t *fpk = search_by_fid(EF_EE_DEV, NULL, SPECIFY_EF);
ret = flash_write_data_to_file(fpk, res_APDU, cvc_len);
if (ret != 0)
return SW_EXEC_ERROR();
-
+
const uint8_t *keyid = (const uint8_t *)"\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0", *label = (const uint8_t *)"ESTERMHSM";
size_t prkd_len = asn1_build_prkd_ecc(label, strlen((const char *)label), keyid, 20, 192, res_APDU, 4096);
fpk = search_by_fid(EF_PRKD_DEV, NULL, SPECIFY_EF);
diff --git a/src/hsm/cmd_key_domain.c b/src/hsm/cmd_key_domain.c
index ee6d655..ce273be 100644
--- a/src/hsm/cmd_key_domain.c
+++ b/src/hsm/cmd_key_domain.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -120,9 +120,9 @@ int cmd_key_domain() {
if (!t86 || t86[0] != 0x4)
return SW_EXEC_ERROR();
size_t t54_len = 0;
- const uint8_t *t54 = cvc_get_field(apdu.data, apdu.nc, &t54_len, 0x54);
+ const uint8_t *t54 = cvc_get_field(apdu.data, apdu.nc, &t54_len, 0x54);
if (!t54)
- return SW_WRONG_DATA();
+ return SW_WRONG_DATA();
uint8_t hash[32], *input = (uint8_t *)calloc(1, (t86_len-1)/2+1);
input[0] = 0x54;
memcpy(input+1, t86+1, (t86_len-1)/2);
@@ -134,7 +134,7 @@ int cmd_key_domain() {
file_t *tf = file_new(EF_XKEK+p2);
if (!tf)
return SW_MEMORY_FAILURE();
-
+
//All checks done. Get Key Domain UID
pub = cvc_get_pub(apdu.data, apdu.nc, &pub_len);
if (pub) {
diff --git a/src/hsm/cmd_key_gen.c b/src/hsm/cmd_key_gen.c
index 2d3725d..949ddb6 100644
--- a/src/hsm/cmd_key_gen.c
+++ b/src/hsm/cmd_key_gen.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "crypto_utils.h"
#include "sc_hsm.h"
#include "random.h"
diff --git a/src/hsm/cmd_key_unwrap.c b/src/hsm/cmd_key_unwrap.c
index fa2070d..c541f2e 100644
--- a/src/hsm/cmd_key_unwrap.c
+++ b/src/hsm/cmd_key_unwrap.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "crypto_utils.h"
#include "sc_hsm.h"
#include "kek.h"
diff --git a/src/hsm/cmd_key_wrap.c b/src/hsm/cmd_key_wrap.c
index 0dac018..5c21faf 100644
--- a/src/hsm/cmd_key_wrap.c
+++ b/src/hsm/cmd_key_wrap.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -71,7 +71,7 @@ int cmd_key_wrap() {
uint8_t kdata[32]; //maximum AES key size
if (wait_button() == true) //timeout
return SW_SECURE_MESSAGE_EXEC_ERROR();
-
+
int key_size = file_get_size(ef), aes_type = HSM_KEY_AES;
memcpy(kdata, file_get_data(ef), key_size);
if (mkek_decrypt(kdata, key_size) != 0) {
diff --git a/src/hsm/cmd_keypair_gen.c b/src/hsm/cmd_keypair_gen.c
index fe776ee..82f3758 100644
--- a/src/hsm/cmd_keypair_gen.c
+++ b/src/hsm/cmd_keypair_gen.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "crypto_utils.h"
#include "sc_hsm.h"
#include "files.h"
@@ -29,7 +29,7 @@ int cmd_keypair_gen() {
if (!isUserAuthenticated)
return SW_SECURITY_STATUS_NOT_SATISFIED();
int ret = 0;
-
+
size_t tout = 0;
//sc_asn1_print_tags(apdu.data, apdu.nc);
uint8_t *p = NULL;
@@ -72,7 +72,7 @@ int cmd_keypair_gen() {
mbedtls_rsa_free(&rsa);
return SW_EXEC_ERROR();
}
- mbedtls_rsa_free(&rsa);
+ mbedtls_rsa_free(&rsa);
}
else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_256,MIN(oid_len,10)) == 0) { //ECC
size_t prime_len;
@@ -131,7 +131,7 @@ int cmd_keypair_gen() {
}
mbedtls_ecdsa_free(&ecdsa);
}
-
+
}
}
else
diff --git a/src/hsm/cmd_list_keys.c b/src/hsm/cmd_list_keys.c
index 84a587f..ea59704 100644
--- a/src/hsm/cmd_list_keys.c
+++ b/src/hsm/cmd_list_keys.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -48,7 +48,7 @@ int cmd_list_keys()
res_APDU[res_APDU_size++] = f->fid & 0xff;
}
}
-
+
for (int i = 0; i < dynamic_files; i++) {
file_t *f = &dynamic_file[i];
if ((f->fid & 0xff00) == (DCOD_PREFIX << 8)) {
diff --git a/src/hsm/cmd_mse.c b/src/hsm/cmd_mse.c
index f3f5e78..c1aa8e4 100644
--- a/src/hsm/cmd_mse.c
+++ b/src/hsm/cmd_mse.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -32,7 +32,7 @@ int cmd_mse() {
if (p1 & 0x1) { //SET
uint16_t tag = 0x0;
uint8_t *tag_data = NULL, *p = NULL;
- size_t tag_len = 0;
+ size_t tag_len = 0;
while (walk_tlv(apdu.data, apdu.nc, &p, &tag, &tag_len, &tag_data)) {
if (tag == 0x80) {
if (p2 == 0xA4) {
@@ -42,7 +42,7 @@ int cmd_mse() {
}
else if (tag == 0x83) {
if (tag_len == 1) {
-
+
}
else {
if (p2 == 0xB6) {
diff --git a/src/hsm/cmd_pso.c b/src/hsm/cmd_pso.c
index 8318b95..48be4fb 100644
--- a/src/hsm/cmd_pso.c
+++ b/src/hsm/cmd_pso.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
#include "oid.h"
#include "asn1.h"
@@ -53,7 +53,7 @@ int cmd_pso() {
flash_write_data_to_file(ca_ef, apdu.data, apdu.nc);
if (add_cert_puk_store(file_get_data(ca_ef), file_get_size(ca_ef), false) != CCID_OK)
return SW_FILE_FULL();
-
+
size_t chr_len = 0;
const uint8_t *chr = cvc_get_chr(apdu.data, apdu.nc, &chr_len);
if (chr == NULL)
diff --git a/src/hsm/cmd_puk_auth.c b/src/hsm/cmd_puk_auth.c
index f3e5e3d..48472b3 100644
--- a/src/hsm/cmd_puk_auth.c
+++ b/src/hsm/cmd_puk_auth.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
#include "files.h"
#include "cvc.h"
diff --git a/src/hsm/cmd_read_binary.c b/src/hsm/cmd_read_binary.c
index f32b79b..48e2af8 100644
--- a/src/hsm/cmd_read_binary.c
+++ b/src/hsm/cmd_read_binary.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -22,7 +22,7 @@ int cmd_read_binary() {
uint32_t offset = 0;
uint8_t ins = INS(apdu), p1 = P1(apdu), p2 = P2(apdu);
const file_t *ef = NULL;
-
+
if ((ins & 0x1) == 0)
{
if ((p1 & 0x80) != 0) {
@@ -39,23 +39,23 @@ int cmd_read_binary() {
if (p1 == 0 && (p2 & 0xE0) == 0 && (p2 & 0x1f) != 0 && (p2 & 0x1f) != 0x1f) {
if (!(ef = search_by_fid(p2&0x1f, NULL, SPECIFY_EF)))
return SW_FILE_NOT_FOUND ();
- }
+ }
else {
uint16_t file_id = make_uint16_t(p1, p2); // & 0x7fff;
if (file_id == 0x0)
ef = currentEF;
else if (!(ef = search_by_fid(file_id, NULL, SPECIFY_EF)) && !(ef = search_dynamic_file(file_id)))
return SW_FILE_NOT_FOUND ();
-
+
if (apdu.data[0] != 0x54)
return SW_WRONG_DATA();
-
+
offset = 0;
for (int d = 0; d < apdu.data[1]; d++)
offset |= apdu.data[2+d]<<(apdu.data[1]-1-d)*8;
- }
+ }
}
-
+
if ((fid >> 8) == KEY_PREFIX || !authenticate_action(ef, ACL_OP_READ_SEARCH)) {
return SW_SECURITY_STATUS_NOT_SATISFIED();
}
@@ -77,7 +77,7 @@ int cmd_read_binary() {
uint16_t data_len = file_get_size(ef);
if (offset > data_len)
return SW_WRONG_P1P2();
-
+
uint16_t maxle = data_len-offset;
if (apdu.ne > maxle)
apdu.ne = maxle;
diff --git a/src/hsm/cmd_reset_retry.c b/src/hsm/cmd_reset_retry.c
index 4dff5f6..cb4a678 100644
--- a/src/hsm/cmd_reset_retry.c
+++ b/src/hsm/cmd_reset_retry.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -21,7 +21,7 @@
int cmd_reset_retry() {
if (P2(apdu) != 0x81)
- return SW_REFERENCE_NOT_FOUND();
+ return SW_REFERENCE_NOT_FOUND();
if (!file_sopin || !file_pin1) {
return SW_FILE_NOT_FOUND();
}
@@ -43,7 +43,7 @@ int cmd_reset_retry() {
has_session_sopin = true;
hash_multi(apdu.data, 8, session_sopin);
}
- else if (P1(apdu) == 0x2) {
+ else if (P1(apdu) == 0x2) {
if (!has_session_sopin)
return SW_CONDITIONS_NOT_SATISFIED();
if (apdu.nc > 16)
@@ -69,7 +69,7 @@ int cmd_reset_retry() {
low_flash_available();
return SW_OK();
}
- else if (P1(apdu) == 0x1 || P1(apdu) == 0x3) {
+ else if (P1(apdu) == 0x1 || P1(apdu) == 0x3) {
if (!(opts & HSM_OPT_RRC_RESET_ONLY))
return SW_COMMAND_NOT_ALLOWED();
if (P1(apdu) == 0x1) {
diff --git a/src/hsm/cmd_select.c b/src/hsm/cmd_select.c
index b966056..e9eaa6c 100644
--- a/src/hsm/cmd_select.c
+++ b/src/hsm/cmd_select.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -42,26 +42,26 @@ int cmd_select() {
uint8_t p2 = P2(apdu);
file_t *pe = NULL;
uint16_t fid = 0x0;
-
- // Only "first or only occurence" supported
+
+ // Only "first or only occurence" supported
//if ((p2 & 0xF3) != 0x00) {
// return SW_INCORRECT_P1P2();
//}
-
+
if (apdu.nc >= 2)
fid = get_uint16_t(apdu.data, 0);
-
+
//if ((fid & 0xff00) == (KEY_PREFIX << 8))
// fid = (PRKD_PREFIX << 8) | (fid & 0xff);
-
+
uint8_t pfx = fid >> 8;
- if (pfx == PRKD_PREFIX ||
- pfx == CD_PREFIX ||
- pfx == CA_CERTIFICATE_PREFIX ||
- pfx == KEY_PREFIX ||
- pfx == EE_CERTIFICATE_PREFIX ||
- pfx == DCOD_PREFIX ||
- pfx == DATA_PREFIX ||
+ if (pfx == PRKD_PREFIX ||
+ pfx == CD_PREFIX ||
+ pfx == CA_CERTIFICATE_PREFIX ||
+ pfx == KEY_PREFIX ||
+ pfx == EE_CERTIFICATE_PREFIX ||
+ pfx == DCOD_PREFIX ||
+ pfx == DATA_PREFIX ||
pfx == PROT_DATA_PREFIX) {
if (!(pe = search_dynamic_file(fid)) && !(pe = search_by_fid(fid, NULL, SPECIFY_EF)))
return SW_FILE_NOT_FOUND();
@@ -98,7 +98,7 @@ int cmd_select() {
}
if (card_terminated) {
return set_res_sw(0x62, 0x85);
- }
+ }
}
else if (p1 == 0x08) { //Select from the MF - Path without the MF identifier
if (!(pe = search_by_path(apdu.data, apdu.nc, MF))) {
diff --git a/src/hsm/cmd_session_pin.c b/src/hsm/cmd_session_pin.c
index cd950f1..4f49f24 100644
--- a/src/hsm/cmd_session_pin.c
+++ b/src/hsm/cmd_session_pin.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
#include "random.h"
#include "eac.h"
@@ -23,7 +23,7 @@ int cmd_session_pin() {
if (P1(apdu) == 0x01 && P2(apdu) == 0x81) {
memcpy(sm_session_pin, random_bytes_get(8), 8);
sm_session_pin_len = 8;
-
+
memcpy(res_APDU, sm_session_pin, sm_session_pin_len);
res_APDU_size = sm_session_pin_len;
apdu.ne = sm_session_pin_len;
diff --git a/src/hsm/cmd_signature.c b/src/hsm/cmd_signature.c
index ce0328c..0aed65a 100644
--- a/src/hsm/cmd_signature.c
+++ b/src/hsm/cmd_signature.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "crypto_utils.h"
#include "sc_hsm.h"
#include "asn1.h"
@@ -94,7 +94,7 @@ int cmd_signature() {
file_t *fkey;
if (!isUserAuthenticated)
return SW_SECURITY_STATUS_NOT_SATISFIED();
- if (!(fkey = search_dynamic_file((KEY_PREFIX << 8) | key_id)) || !fkey->data || file_get_size(fkey) == 0)
+ if (!(fkey = search_dynamic_file((KEY_PREFIX << 8) | key_id)) || !fkey->data || file_get_size(fkey) == 0)
return SW_FILE_NOT_FOUND();
if (get_key_counter(fkey) == 0)
return SW_FILE_FULL();
@@ -114,7 +114,7 @@ int cmd_signature() {
if (p2 >= ALGO_RSA_RAW && p2 <= ALGO_RSA_PSS_SHA512) {
mbedtls_rsa_context ctx;
mbedtls_rsa_init(&ctx);
-
+
int r;
r = load_private_key_rsa(&ctx, fkey);
if (r != CCID_OK) {
@@ -144,15 +144,15 @@ int cmd_signature() {
asn1_find_tag(p, tout, 0x4, &hash_len, &hash);
}
if (oid && oid_len > 0) {
- if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA1, oid_len) == 0)
+ if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
- else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA224, oid_len) == 0)
+ else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA224, oid_len) == 0)
md = MBEDTLS_MD_SHA224;
- else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA256, oid_len) == 0)
+ else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA256, oid_len) == 0)
md = MBEDTLS_MD_SHA256;
- else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA384, oid_len) == 0)
+ else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA384, oid_len) == 0)
md = MBEDTLS_MD_SHA384;
- else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA512, oid_len) == 0)
+ else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA512, oid_len) == 0)
md = MBEDTLS_MD_SHA512;
}
if (p2 >= ALGO_RSA_PSS && p2 <= ALGO_RSA_PSS_SHA512) {
diff --git a/src/hsm/cmd_update_ef.c b/src/hsm/cmd_update_ef.c
index f5b61ac..55aff01 100644
--- a/src/hsm/cmd_update_ef.c
+++ b/src/hsm/cmd_update_ef.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
#include "asn1.h"
@@ -33,19 +33,19 @@ int cmd_update_ef() {
ef = currentEF;
else if (p1 != EE_CERTIFICATE_PREFIX && p1 != PRKD_PREFIX && p1 != CA_CERTIFICATE_PREFIX && p1 != CD_PREFIX && p1 != DATA_PREFIX && p1 != DCOD_PREFIX && p1 != PROT_DATA_PREFIX)
return SW_INCORRECT_P1P2();
-
+
if (ef && !authenticate_action(ef, ACL_OP_UPDATE_ERASE))
return SW_SECURITY_STATUS_NOT_SATISFIED();
-
+
uint16_t tag = 0x0;
uint8_t *tag_data = NULL, *p = NULL;
- size_t tag_len = 0;
+ size_t tag_len = 0;
while (walk_tlv(apdu.data, apdu.nc, &p, &tag, &tag_len, &tag_data)) {
if (tag == 0x54) { //ofset tag
for (int i = 1; i <= tag_len; i++)
offset |= (*tag_data++ << (8*(tag_len-i)));
}
- else if (tag == 0x53) { //data
+ else if (tag == 0x53) { //data
data_len = tag_len;
data = tag_data;
}
@@ -71,7 +71,7 @@ int cmd_update_ef() {
else {
if (!ef->data)
return SW_DATA_INVALID();
-
+
uint8_t *data_merge = (uint8_t *)calloc(1, offset+data_len);
memcpy(data_merge, file_get_data(ef), offset);
memcpy(data_merge+offset, data, data_len);
@@ -82,5 +82,5 @@ int cmd_update_ef() {
}
low_flash_available();
}
- return SW_OK();
+ return SW_OK();
}
diff --git a/src/hsm/cmd_verify.c b/src/hsm/cmd_verify.c
index 33436a9..7a21611 100644
--- a/src/hsm/cmd_verify.c
+++ b/src/hsm/cmd_verify.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -20,7 +20,7 @@
int cmd_verify() {
uint8_t p1 = P1(apdu);
uint8_t p2 = P2(apdu);
-
+
if (p1 != 0x0 || (p2 & 0x60) != 0x0)
return SW_WRONG_P1P2();
diff --git a/src/hsm/cvc.c b/src/hsm/cvc.c
index 4c00c08..f65fbed 100644
--- a/src/hsm/cvc.c
+++ b/src/hsm/cvc.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -126,7 +126,7 @@ size_t asn1_cvc_cert_body(void *rsa_ecdsa, uint8_t key_type, uint8_t *buf, size_
uint8_t *car = NULL, *chr = NULL;
size_t lencar = 0, lenchr = 0;
-
+
if (asn1_find_tag(apdu.data, apdu.nc, 0x42, &lencar, &car) == false || lencar == 0 || car == NULL) {
car = (uint8_t *)dev_name;
lencar = dev_name_len;
@@ -136,9 +136,9 @@ size_t asn1_cvc_cert_body(void *rsa_ecdsa, uint8_t key_type, uint8_t *buf, size_
lenchr = dev_name_len;
}
size_t car_size = asn1_len_tag(0x42, lencar), chr_size = asn1_len_tag(0x5f20, lenchr);
-
+
size_t tot_len = asn1_len_tag(0x7f4e, cpi_size+car_size+pubkey_size+chr_size+ext_size);
-
+
if (buf_len == 0 || buf == NULL)
return tot_len;
if (buf_len < tot_len)
@@ -283,14 +283,14 @@ size_t asn1_build_cert_description(const uint8_t *label, size_t label_len, const
*p++ = 0x3;
p += format_tlv_len(opt_len, p);
memcpy(p, "\x06\x40", 2); p += 2;
-
+
//Seq 2
*p++ = 0x30;
p += format_tlv_len(asn1_len_tag(0x4, 20), p);
*p++ = 0x4;
p += format_tlv_len(20, p);
mbedtls_md(mbedtls_md_info_from_type(MBEDTLS_MD_SHA1), puk, puk_len, p); p += 20;
-
+
//Seq 3
*p++ = 0xA1;
p += format_tlv_len(asn1_len_tag(0x30, asn1_len_tag(0x30, asn1_len_tag(0x4, sizeof(uint16_t)))), p);
@@ -323,7 +323,7 @@ size_t asn1_build_prkd_ecc(const uint8_t *label, size_t label_len, const uint8_t
*p++ = 0xC;
p += format_tlv_len(label_len, p);
memcpy(p, label, label_len); p += label_len;
-
+
//Seq 2
*p++ = 0x30;
p += format_tlv_len(asn1_len_tag(0x4, keyid_len)+asn1_len_tag(0x3, 3), p);
@@ -333,7 +333,7 @@ size_t asn1_build_prkd_ecc(const uint8_t *label, size_t label_len, const uint8_t
*p++ = 0x3;
p += format_tlv_len(3, p);
memcpy(p, "\x07\x20\x80", 3); p += 3;
-
+
//Seq 3
*p++ = 0xA1;
p += format_tlv_len(asn1_len_tag(0x30, asn1_len_tag(0x30, asn1_len_tag(0x4, 0))+asn1_len_tag(0x2,2)), p);
@@ -444,7 +444,7 @@ mbedtls_ecp_group_id cvc_inherite_ec_group(const uint8_t *ca, size_t ca_len) {
const uint8_t *t81 = cvc_get_field(ca_puk, ca_puk_len, &t81_len, 0x81);
if (!t81)
return MBEDTLS_ECP_DP_NONE;
-
+
return ec_get_curve_from_prime(t81, t81_len);
}
@@ -465,11 +465,11 @@ int puk_verify(const uint8_t *sig, size_t sig_len, const uint8_t *hash, size_t h
mbedtls_rsa_context rsa;
mbedtls_rsa_init(&rsa);
mbedtls_md_type_t md = MBEDTLS_MD_NONE;
- if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_1, oid_len) == 0)
+ if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
- else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_256, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_256, oid_len) == 0)
md = MBEDTLS_MD_SHA256;
- else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_512, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_512, oid_len) == 0)
md = MBEDTLS_MD_SHA512;
else if (memcmp(oid, OID_ID_TA_RSA_PSS_SHA_1, oid_len) == 0) {
md = MBEDTLS_MD_SHA1;
@@ -514,19 +514,19 @@ int puk_verify(const uint8_t *sig, size_t sig_len, const uint8_t *hash, size_t h
}
else if (memcmp(oid, OID_ID_TA_ECDSA, 9) == 0) { //ECC
mbedtls_md_type_t md = MBEDTLS_MD_NONE;
- if (memcmp(oid, OID_ID_TA_ECDSA_SHA_1, oid_len) == 0)
+ if (memcmp(oid, OID_ID_TA_ECDSA_SHA_1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_224, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_224, oid_len) == 0)
md = MBEDTLS_MD_SHA224;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_256, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_256, oid_len) == 0)
md = MBEDTLS_MD_SHA256;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_384, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_384, oid_len) == 0)
md = MBEDTLS_MD_SHA384;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_512, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_512, oid_len) == 0)
md = MBEDTLS_MD_SHA512;
- if (md == MBEDTLS_MD_NONE)
+ if (md == MBEDTLS_MD_NONE)
return CCID_WRONG_DATA;
-
+
size_t t86_len = 0;
const uint8_t *t86 = cvc_get_field(puk, puk_len, &t86_len, 0x86);
if (!t86)
@@ -595,11 +595,11 @@ int cvc_verify(const uint8_t *cert, size_t cert_len, const uint8_t *ca, size_t c
return CCID_WRONG_DATA;
mbedtls_md_type_t md = MBEDTLS_MD_NONE;
if (memcmp(oid, OID_ID_TA_RSA, 9) == 0) { //RSA
- if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_1, oid_len) == 0)
+ if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
- else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_256, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_256, oid_len) == 0)
md = MBEDTLS_MD_SHA256;
- else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_512, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_512, oid_len) == 0)
md = MBEDTLS_MD_SHA512;
else if (memcmp(oid, OID_ID_TA_RSA_PSS_SHA_1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
@@ -609,18 +609,18 @@ int cvc_verify(const uint8_t *cert, size_t cert_len, const uint8_t *ca, size_t c
md = MBEDTLS_MD_SHA512;
}
else if (memcmp(oid, OID_ID_TA_ECDSA, 9) == 0) { //ECC
- if (memcmp(oid, OID_ID_TA_ECDSA_SHA_1, oid_len) == 0)
+ if (memcmp(oid, OID_ID_TA_ECDSA_SHA_1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_224, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_224, oid_len) == 0)
md = MBEDTLS_MD_SHA224;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_256, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_256, oid_len) == 0)
md = MBEDTLS_MD_SHA256;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_384, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_384, oid_len) == 0)
md = MBEDTLS_MD_SHA384;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_512, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_512, oid_len) == 0)
md = MBEDTLS_MD_SHA512;
}
- if (md == MBEDTLS_MD_NONE)
+ if (md == MBEDTLS_MD_NONE)
return CCID_WRONG_DATA;
const mbedtls_md_info_t *md_info = mbedtls_md_info_from_type(md);
uint8_t hash[64], hash_len = mbedtls_md_get_size(md_info);
diff --git a/src/hsm/cvc.h b/src/hsm/cvc.h
index 90c2774..c5babfe 100644
--- a/src/hsm/cvc.h
+++ b/src/hsm/cvc.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/files.c b/src/hsm/files.c
index d1d7eb8..a00bdf6 100644
--- a/src/hsm/files.c
+++ b/src/hsm/files.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/files.h b/src/hsm/files.h
index 0b8d772..6090d55 100644
--- a/src/hsm/files.h
+++ b/src/hsm/files.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/kek.c b/src/hsm/kek.c
index 0a06655..8af6bf3 100644
--- a/src/hsm/kek.c
+++ b/src/hsm/kek.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -215,7 +215,7 @@ int mkek_decrypt(uint8_t *data, size_t len) {
int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_t *out_len, const uint8_t *allowed, size_t allowed_len) {
if (!(key_type & HSM_KEY_RSA) && !(key_type & HSM_KEY_EC) && !(key_type & HSM_KEY_AES))
return CCID_WRONG_DATA;
-
+
uint8_t kb[8+2*4+2*4096/8+3+13]; //worst case: RSA-4096 (plus, 13 bytes padding)
memset(kb, 0, sizeof(kb));
int kb_len = 0, r = 0;
@@ -226,19 +226,19 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
r = dkek_kenc(id, kenc);
if (r != CCID_OK)
return r;
-
+
uint8_t kcv[8];
memset(kcv, 0, sizeof(kcv));
r = dkek_kcv(id, kcv);
if (r != CCID_OK)
return r;
-
+
uint8_t kmac[32];
memset(kmac, 0, sizeof(kmac));
r = dkek_kmac(id, kmac);
if (r != CCID_OK)
return r;
-
+
if (key_type & HSM_KEY_AES) {
if (key_type & HSM_KEY_AES_128)
kb_len = 16;
@@ -246,38 +246,38 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
kb_len = 24;
else if (key_type & HSM_KEY_AES_256)
kb_len = 32;
-
+
if (kb_len != 16 && kb_len != 24 && kb_len != 32)
return CCID_WRONG_DATA;
if (*out_len < 8+1+10+6+4+(2+32+14)+16)
return CCID_WRONG_LENGTH;
-
+
put_uint16_t(kb_len, kb+8);
memcpy(kb+10, key_ctx, kb_len);
kb_len += 2;
-
+
algo = (uint8_t *)"\x00\x08\x60\x86\x48\x01\x65\x03\x04\x01"; //2.16.840.1.101.3.4.1 (2+8)
algo_len = 10;
}
else if (key_type & HSM_KEY_RSA) {
- if (*out_len < 8+1+12+6+(8+2*4+2*4096/8+3+13)+16) //13 bytes pading
+ if (*out_len < 8+1+12+6+(8+2*4+2*4096/8+3+13)+16) //13 bytes pading
return CCID_WRONG_LENGTH;
mbedtls_rsa_context *rsa = (mbedtls_rsa_context *)key_ctx;
kb_len = 0;
put_uint16_t(mbedtls_rsa_get_len(rsa)*8, kb+8+kb_len); kb_len += 2;
-
+
put_uint16_t(mbedtls_mpi_size(&rsa->D), kb+8+kb_len); kb_len += 2;
mbedtls_mpi_write_binary(&rsa->D, kb+8+kb_len, mbedtls_mpi_size(&rsa->D)); kb_len += mbedtls_mpi_size(&rsa->D);
put_uint16_t(mbedtls_mpi_size(&rsa->N), kb+8+kb_len); kb_len += 2;
mbedtls_mpi_write_binary(&rsa->N, kb+8+kb_len, mbedtls_mpi_size(&rsa->N)); kb_len += mbedtls_mpi_size(&rsa->N);
put_uint16_t(mbedtls_mpi_size(&rsa->E), kb+8+kb_len); kb_len += 2;
mbedtls_mpi_write_binary(&rsa->E, kb+8+kb_len, mbedtls_mpi_size(&rsa->E)); kb_len += mbedtls_mpi_size(&rsa->E);
-
+
algo = (uint8_t *)"\x00\x0A\x04\x00\x7F\x00\x07\x02\x02\x02\x01\x02";
algo_len = 12;
}
else if (key_type & HSM_KEY_EC) {
- if (*out_len < 8+1+12+6+(8+2*8+9*66+2+4)+16) //4 bytes pading
+ if (*out_len < 8+1+12+6+(8+2*8+9*66+2+4)+16) //4 bytes pading
return CCID_WRONG_LENGTH;
mbedtls_ecdsa_context *ecdsa = (mbedtls_ecdsa_context *)key_ctx;
kb_len = 0;
@@ -300,16 +300,16 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
kb[8+kb_len++] = 0x4;
mbedtls_mpi_write_binary(&ecdsa->Q.X, kb+8+kb_len, mbedtls_mpi_size(&ecdsa->Q.X)); kb_len += mbedtls_mpi_size(&ecdsa->Q.X);
mbedtls_mpi_write_binary(&ecdsa->Q.Y, kb+8+kb_len, mbedtls_mpi_size(&ecdsa->Q.Y)); kb_len += mbedtls_mpi_size(&ecdsa->Q.Y);
-
+
algo = (uint8_t *)"\x00\x0A\x04\x00\x7F\x00\x07\x02\x02\x02\x02\x03";
algo_len = 12;
}
memset(out, 0, *out_len);
*out_len = 0;
-
+
memcpy(out+*out_len, kcv, 8);
*out_len += 8;
-
+
if (key_type & HSM_KEY_AES)
out[*out_len] = 15;
else if (key_type & HSM_KEY_RSA)
@@ -317,14 +317,14 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
else if (key_type & HSM_KEY_EC)
out[*out_len] = 12;
*out_len += 1;
-
+
if (algo) {
memcpy(out+*out_len, algo, algo_len);
*out_len += algo_len;
}
else
*out_len += 2;
-
+
if (allowed && allowed_len > 0) {
put_uint16_t(allowed_len, out+*out_len); *out_len += 2;
memcpy(out+*out_len, allowed, allowed_len);
@@ -334,7 +334,7 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
*out_len += 2;
//add 4 zeros
*out_len += 4;
-
+
memcpy(kb, random_bytes_get(8), 8);
kb_len += 8; //8 random bytes
int kb_len_pad = ((int)(kb_len/16))*16;
@@ -347,12 +347,12 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
r = aes_encrypt(kenc, NULL, 256, HSM_AES_MODE_CBC, kb, kb_len_pad);
if (r != CCID_OK)
return r;
-
+
memcpy(out+*out_len, kb, kb_len_pad);
*out_len += kb_len_pad;
r = mbedtls_cipher_cmac(mbedtls_cipher_info_from_type(MBEDTLS_CIPHER_AES_256_ECB), kmac, 256, out, *out_len, out+*out_len);
-
+
*out_len += 16;
if (r != 0)
return r;
@@ -376,62 +376,62 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
r = dkek_kcv(id, kcv);
if (r != CCID_OK)
return r;
-
+
uint8_t kmac[32];
memset(kmac, 0, sizeof(kmac));
r = dkek_kmac(id, kmac);
if (r != CCID_OK)
return r;
-
+
uint8_t kenc[32];
memset(kenc, 0, sizeof(kenc));
r = dkek_kenc(id, kenc);
if (r != CCID_OK)
return r;
-
+
if (memcmp(kcv, in, 8) != 0)
return CCID_WRONG_DKEK;
-
+
uint8_t signature[16];
r = mbedtls_cipher_cmac(mbedtls_cipher_info_from_type(MBEDTLS_CIPHER_AES_256_ECB), kmac, 256, in, in_len-16, signature);
if (r != 0)
return CCID_WRONG_SIGNATURE;
if (memcmp(signature, in+in_len-16, 16) != 0)
return CCID_WRONG_SIGNATURE;
-
+
int key_type = in[8];
if (key_type != 5 && key_type != 6 && key_type != 12 && key_type != 15)
return CCID_WRONG_DATA;
-
+
if ((key_type == 5 || key_type == 6) && memcmp(in+9, "\x00\x0A\x04\x00\x7F\x00\x07\x02\x02\x02\x01\x02", 12) != 0)
return CCID_WRONG_DATA;
-
+
if (key_type == 12 && memcmp(in+9, "\x00\x0A\x04\x00\x7F\x00\x07\x02\x02\x02\x02\x03", 12) != 0)
return CCID_WRONG_DATA;
-
+
if (key_type == 15 && memcmp(in+9, "\x00\x08\x60\x86\x48\x01\x65\x03\x04\x01", 10) != 0)
return CCID_WRONG_DATA;
-
+
size_t ofs = 9;
-
+
//OID
size_t len = get_uint16_t(in, ofs);
ofs += len+2;
-
+
//Allowed algorithms
len = get_uint16_t(in, ofs);
*allowed = (uint8_t *)(in+ofs+2);
*allowed_len = len;
ofs += len+2;
-
+
//Access conditions
len = get_uint16_t(in, ofs);
ofs += len+2;
-
+
//Key OID
len = get_uint16_t(in, ofs);
ofs += len+2;
-
+
if ((in_len-16-ofs) % 16 != 0)
return CCID_WRONG_PADDING;
uint8_t kb[8+2*4+2*4096/8+3+13]; //worst case: RSA-4096 (plus, 13 bytes padding)
@@ -440,7 +440,7 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
r = aes_decrypt(kenc, NULL, 256, HSM_AES_MODE_CBC, kb, in_len-16-ofs);
if (r != CCID_OK)
return r;
-
+
int key_size = get_uint16_t(kb, 8);
if (key_size_out)
*key_size_out = key_size;
@@ -455,7 +455,7 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
mbedtls_rsa_free(rsa);
return CCID_WRONG_DATA;
}
-
+
len = get_uint16_t(kb, ofs); ofs += 2;
r = mbedtls_mpi_read_binary(&rsa->N, kb+ofs, len); ofs += len;
if (r != 0) {
@@ -466,20 +466,20 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
else if (key_type == 6) {
//DP-1
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
//DQ-1
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
len = get_uint16_t(kb, ofs); ofs += 2;
r = mbedtls_mpi_read_binary(&rsa->P, kb+ofs, len); ofs += len;
if (r != 0) {
mbedtls_rsa_free(rsa);
return CCID_WRONG_DATA;
}
-
+
//PQ
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
len = get_uint16_t(kb, ofs); ofs += 2;
r = mbedtls_mpi_read_binary(&rsa->Q, kb+ofs, len); ofs += len;
if (r != 0) {
@@ -489,14 +489,14 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
//N
len = get_uint16_t(kb, ofs); ofs += len+2;
}
-
+
len = get_uint16_t(kb, ofs); ofs += 2;
r = mbedtls_mpi_read_binary(&rsa->E, kb+ofs, len); ofs += len;
if (r != 0) {
mbedtls_rsa_free(rsa);
return CCID_WRONG_DATA;
}
-
+
if (key_type == 5) {
r = mbedtls_rsa_import(rsa, &rsa->N, NULL, NULL, &rsa->D, &rsa->E);
if (r != 0) {
@@ -511,7 +511,7 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
return CCID_EXEC_ERROR;
}
}
-
+
r = mbedtls_rsa_complete(rsa);
if (r != 0) {
mbedtls_rsa_free(rsa);
@@ -526,13 +526,13 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
else if (key_type == 12) {
mbedtls_ecdsa_context *ecdsa = (mbedtls_ecdsa_context *)key_ctx;
mbedtls_ecdsa_init(ecdsa);
-
+
//A
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
//B
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
//P
len = get_uint16_t(kb, ofs); ofs += 2;
mbedtls_ecp_group_id ec_id = ec_get_curve_from_prime(kb+ofs, len);
@@ -541,13 +541,13 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
return CCID_WRONG_DATA;
}
ofs += len;
-
+
//N
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
//G
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
//d
len = get_uint16_t(kb, ofs); ofs += 2;
r = mbedtls_ecp_read_key(ec_id, ecdsa, kb+ofs, len);
diff --git a/src/hsm/kek.h b/src/hsm/kek.h
index cd18240..8a0e5d1 100644
--- a/src/hsm/kek.h
+++ b/src/hsm/kek.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/oid.c b/src/hsm/oid.c
index 56d2da0..f7395c2 100644
--- a/src/hsm/oid.c
+++ b/src/hsm/oid.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/oid.h b/src/hsm/oid.h
index e758f7c..c59063f 100644
--- a/src/hsm/oid.h
+++ b/src/hsm/oid.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -70,7 +70,7 @@
#define OID_ID_RI_DH_SHA_224 OID_ID_RI_DH "\x02"
#define OID_ID_RI_DH_SHA_256 OID_ID_RI_DH "\x03"
-#define OID_ID_RI_ECDH OID_ID_RI "\x02"
+#define OID_ID_RI_ECDH OID_ID_RI "\x02"
#define OID_ID_RI_ECDH_SHA_1 OID_ID_RI_ECDH "\x01"
#define OID_ID_RI_ECDH_SHA_224 OID_ID_RI_ECDH "\x02"
diff --git a/src/hsm/sc_hsm.c b/src/hsm/sc_hsm.c
index 803ffb9..de25bdb 100644
--- a/src/hsm/sc_hsm.c
+++ b/src/hsm/sc_hsm.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -26,13 +26,13 @@
#include "asn1.h"
const uint8_t sc_hsm_aid[] = {
- 11,
+ 11,
0xE8,0x2B,0x06,0x01,0x04,0x01,0x81,0xC3,0x1F,0x02,0x01
};
-const uint8_t atr_sc_hsm[] = {
+const uint8_t atr_sc_hsm[] = {
24,
- 0x3B,0xFE,0x18,0x00,0x00,0x81,0x31,0xFE,0x45,0x80,0x31,0x81,0x54,0x48,0x53,0x4D,0x31,0x73,0x80,0x21,0x40,0x81,0x07,0xFA
+ 0x3B,0xFE,0x18,0x00,0x00,0x81,0x31,0xFE,0x45,0x80,0x31,0x81,0x54,0x48,0x53,0x4D,0x31,0x73,0x80,0x21,0x40,0x81,0x07,0xFA
};
uint8_t session_pin[32], session_sopin[32];
@@ -84,7 +84,7 @@ app_t *sc_hsm_select_aid(app_t *a) {
return NULL;
}
-void __attribute__ ((constructor)) sc_hsm_ctor() {
+void __attribute__ ((constructor)) sc_hsm_ctor() {
ccid_atr = atr_sc_hsm;
register_app(sc_hsm_select_aid);
}
@@ -135,7 +135,7 @@ void scan_files() {
printf("FATAL ERROR: Retries SOPIN not found in memory!\r\n");
}
file_t *tf = NULL;
-
+
tf = search_by_fid(0x1082, NULL, SPECIFY_EF);
if (tf) {
if (!tf->data) {
@@ -176,7 +176,7 @@ int add_cert_puk_store(const uint8_t *data, size_t data_len, bool copy) {
return CCID_ERR_NULL_PARAM;
if (puk_store_entries == MAX_PUK_STORE_ENTRIES)
return CCID_ERR_MEMORY_FATAL;
-
+
puk_store[puk_store_entries].copied = copy;
if (copy == true) {
uint8_t *tmp = (uint8_t *)calloc(data_len, sizeof(uint8_t));
@@ -189,7 +189,7 @@ int add_cert_puk_store(const uint8_t *data, size_t data_len, bool copy) {
puk_store[puk_store_entries].chr = cvc_get_chr(puk_store[puk_store_entries].cvcert, data_len, &puk_store[puk_store_entries].chr_len);
puk_store[puk_store_entries].car = cvc_get_car(puk_store[puk_store_entries].cvcert, data_len, &puk_store[puk_store_entries].car_len);
puk_store[puk_store_entries].puk = cvc_get_pub(puk_store[puk_store_entries].cvcert, data_len, &puk_store[puk_store_entries].puk_len);
-
+
puk_store_entries++;
return CCID_OK;
}
@@ -278,7 +278,7 @@ int parse_token_info(const file_t *f, int mode) {
int pin_reset_retries(const file_t *pin, bool force) {
if (!pin)
- return CCID_ERR_NULL_PARAM;
+ return CCID_ERR_NULL_PARAM;
const file_t *max = search_by_fid(pin->fid+1, NULL, SPECIFY_EF);
const file_t *act = search_by_fid(pin->fid+2, NULL, SPECIFY_EF);
if (!max || !act)
@@ -294,7 +294,7 @@ int pin_reset_retries(const file_t *pin, bool force) {
int pin_wrong_retry(const file_t *pin) {
if (!pin)
- return CCID_ERR_NULL_PARAM;
+ return CCID_ERR_NULL_PARAM;
const file_t *act = search_by_fid(pin->fid+2, NULL, SPECIFY_EF);
if (!act)
return CCID_ERR_FILE_NOT_FOUND;
@@ -381,7 +381,7 @@ uint32_t get_key_counter(file_t *fkey) {
const uint8_t *meta_tag = get_meta_tag(fkey, 0x90, &tag_len);
if (meta_tag)
return (meta_tag[0] << 24) | (meta_tag[1] << 16) | (meta_tag[2] << 8) | meta_tag[3];
- return 0xffffffff;
+ return 0xffffffff;
}
bool key_has_purpose(file_t *ef, uint8_t purpose) {
@@ -417,7 +417,7 @@ uint32_t decrement_key_counter(file_t *fkey) {
tag_data[1] = (val >> 16) & 0xff;
tag_data[2] = (val >> 8) & 0xff;
tag_data[3] = val & 0xff;
-
+
int r = meta_add(fkey->fid, cmeta, meta_size);
free(cmeta);
if (r != 0)
@@ -525,7 +525,7 @@ int find_and_store_meta_key(uint8_t key_id) {
int load_private_key_rsa(mbedtls_rsa_context *ctx, file_t *fkey) {
if (wait_button() == true) //timeout
return CCID_VERIFICATION_FAILED;
-
+
int key_size = file_get_size(fkey);
uint8_t kdata[4096/8];
memcpy(kdata, file_get_data(fkey), key_size);
@@ -568,7 +568,7 @@ int load_private_key_rsa(mbedtls_rsa_context *ctx, file_t *fkey) {
int load_private_key_ecdsa(mbedtls_ecdsa_context *ctx, file_t *fkey) {
if (wait_button() == true) //timeout
return CCID_VERIFICATION_FAILED;
-
+
int key_size = file_get_size(fkey);
uint8_t kdata[67]; //Worst case, 521 bit + 1byte
memcpy(kdata, file_get_data(fkey), key_size);
@@ -622,7 +622,7 @@ typedef struct cmd
static const cmd_t cmds[] = {
{ INS_SELECT_FILE, cmd_select },
- { INS_LIST_KEYS, cmd_list_keys },
+ { INS_LIST_KEYS, cmd_list_keys },
{ INS_READ_BINARY, cmd_read_binary },
{ INS_READ_BINARY_ODD, cmd_read_binary },
{ INS_VERIFY, cmd_verify },
diff --git a/src/hsm/sc_hsm.h b/src/hsm/sc_hsm.h
index a031f77..98391f8 100644
--- a/src/hsm/sc_hsm.h
+++ b/src/hsm/sc_hsm.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/version.h b/src/hsm/version.h
index 5e0421a..792e9af 100644
--- a/src/hsm/version.h
+++ b/src/hsm/version.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/workflows/autobuild.sh b/workflows/autobuild.sh
index eb65ec6..09ef1c7 100755
--- a/workflows/autobuild.sh
+++ b/workflows/autobuild.sh
@@ -10,4 +10,4 @@ cd ..
mkdir build
cd build
cmake -DPICO_SDK_PATH=../pico-sdk ..
-make
+make
@@ -64,17 +64,17 @@ From now on, you have full access and can operate normally with the primary devi
Pico HSM uses the PIN to protect the DKEK, which is lately used to protect private/secret keys and wrap/unwrap. However, when PKA is enabled, the authentication is not performed by introducing any PIN.
Authenticated privileges are granted when PKA succeeds, regardless of PIN, which is optional.
-Nevertheless, **it is extremely recommended to combine PKA with PIN**. Note that when combined, only PKA grants authenticated privileges. Therefore, if both schemes are setup, it is necessary to unlock the DKEK with PIN verification.
+Nevertheless, **it is extremely recommended to combine PKA with PIN**. Note that when combined, only PKA grants authenticated privileges. Therefore, if both schemes are setup, it is necessary to unlock the DKEK with PIN verification.
Otherwise, it will not be possible to operate with private/secret keys despite the user will be logged in.
With this scheme, multiple custodians may authenticate the device individually and remotely and, when fully authenticated, the master user can unlock the DKEK with the PIN.
-Moreover, with this approach the device is kept safe and neither the DKEK nor the private/secret keys are stored in plain text in the device.
+Moreover, with this approach the device is kept safe and neither the DKEK nor the private/secret keys are stored in plain text in the device.
Even though the flash memory is dumped by an attacker, it will not be possible to decipher any sensitive data or key.
Initialization of the device with PKA **and** PIN can be achieved with SCS3 or OpenSC:
-**Note:** do not import any DKEK share or DKEK operation before PKA and PIN setup.
+**Note:** do not import any DKEK share or DKEK operation before PKA and PIN setup.
### With OpenSC
@@ -84,9 +84,9 @@ Use the following command (or similar), which accepts the use of PIN parameter *
sc-hsm-tool -X --so-pin 1234567890123456 --pin 648219 -K 1 -n 1 -s 1
```
-and PKA and PIN are enabled, jointly with DKEK protection.
+and PKA and PIN are enabled, jointly with DKEK protection.
-### With SCS3
+###�With SCS3
Unfortunately, SCS3 does not allow to initialize the device with PKA and PIN at the same time, though it can be achieved in separated steps:
@@ -94,4 +94,4 @@ Unfortunately, SCS3 does not allow to initialize the device with PKA and PIN at
2. There is NO default PIN. So, DO NOT attempt to log in yet. A reset PIN shall be requested.
3. Click on ``Reset User-PIN``, introduce the SO-PIN configured during the initialization and introduce the desired User-PIN.
-When done, the device will be configured with PIN **and** PKA.
+When done, the device will be configured with PIN **and** PKA.
diff --git a/doc/scs3.md b/doc/scs3.md
index 92573e1..8dd9dbe 100644
--- a/doc/scs3.md
+++ b/doc/scs3.md
@@ -4,11 +4,11 @@ SCS3 tool is a specific tool developed by CardContact to manage HSM. Thanks to i
- Import PKCS12 private keys and certificates.
- Import private keys and certificates from other Pico HSM devices in WKY format.
--
+-
Unfortunately, there is no pkcs11 tool or equivalent capable to perform the import. Since it uses the SC-HSM driver, it also supports the communication with the [SCS3 tool](https://www.openscdp.org/scsh3/ "SCS3 tool"). It can be downloaded from [here](https://www.openscdp.org/scsh3/download.html "here").
-However, SCS3 only works with those HSM manufactured by CardContact. The check is performed by means of trust store against the manufacturing certificates. For obvious reasons, these certificates can only be signed with the private keys of the Certificate Authorities listed in the trust store.
+However, SCS3 only works with those HSM manufactured by CardContact. The check is performed by means of trust store against the manufacturing certificates. For obvious reasons, these certificates can only be signed with the private keys of the Certificate Authorities listed in the trust store.
Pico HSM is shipped with its own CA certificates. To load this certificate onto the trust store of SCS3, the following line has to be appended to `SmartCardHSM.rootCerts` variable, near line `235` in the file `scs3/scsh/sc-hsm/SmartCardHSM.js`.
@@ -39,8 +39,8 @@ After this ammendment, the program can be started and the KeyManager can be invo
>load("keymanager/keymanager.js");
SmartCard-HSM Version 1.6 on JCOP Free memory 217104 byte
-Issuer Certificate : CVC id-AT DV (official domestic) CAR=ESCVCAHSM00001 CHR=ESDVCAHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2025
-Device Certificate : CVC id-AT Terminal CAR=ESDVCAHSM00001 CHR=ESTERMHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2023
+Issuer Certificate : CVC id-AT DV (official domestic) CAR=ESCVCAHSM00001 CHR=ESDVCAHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2025
+Device Certificate : CVC id-AT Terminal CAR=ESDVCAHSM00001 CHR=ESTERMHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2023
Default Key Domain : 0F89B400975EDD2D425ABF85F2FBD318779B3D85475E65D4
-------------------------------------------------------------------
Please right-click on nodes in the outline to see possible actions.
@@ -60,7 +60,7 @@ It can be executed in a Terminal via
```
## DKEK requirement
-In order to perform the import, private keys must be wrapped with the same DKEK present in the Pico HSM. Thus, the Pico HSM must be previously initialized with at minimum of 1 DKEK share. This share will be used to wrap the private key before import.
+In order to perform the import, private keys must be wrapped with the same DKEK present in the Pico HSM. Thus, the Pico HSM must be previously initialized with at minimum of 1 DKEK share. This share will be used to wrap the private key before import.
Note that the DKEK share shall be available before the import. In this way, all custodians must be present during the import process, since they will have to introduce their respective DKEK.
diff --git a/doc/sign-verify.md b/doc/sign-verify.md
index 1c668e7..c7c1c93 100644
--- a/doc/sign-verify.md
+++ b/doc/sign-verify.md
@@ -1,7 +1,7 @@
# Sign and verify
Pico HSM supports in place signature of arbitrary data. It supports the following algorithms:
-* RSA-PKCS
+* RSA-PKCS
* RSA-X-509
* SHA1-RSA-PKCS
* SHA256-RSA-PKCS
@@ -32,7 +32,7 @@ $ openssl rsa -inform DER -outform PEM -in 1.der -pubin > 1.pub
At this moment, you are able to verify with the public key in `1.pub`. The signature is computed inside the Pico HSM with the private key. It never leaves the device.
## RSA-PKCS
-This algorithm is used to sign raw data.
+This algorithm is used to sign raw data.
To sign the data:
```
@@ -91,7 +91,7 @@ This algorithm uses the RSA-PKCS with PSS salt to randomize the signature. Pico
To sign the data:
```
$ pkcs11-tool --id 1 --sign --pin 648219 --mechanism RSA-PKCS-PSS -i data.sha1 -o data.sig
-```
+```
To verify the signature:
```
@@ -105,7 +105,7 @@ This algorithm takes the file as the input and sends its hash for signing with t
To sign the data:
```
$ pkcs11-tool --id 1 --sign --pin 648219 --mechanism SHA1-RSA-PKCS-PSS -i data -o data.sig
-```
+```
To verify the signature:
```
@@ -118,14 +118,14 @@ This is a raw ECDSA signature, which is usually used to sign a hashed message. `
To sign the data:
```
-$ pkcs11-tool --id 11 --sign --pin 648219 --mechanism ECDSA -i data.sha1 -o data.sig --signature-format openssl
+$ pkcs11-tool --id 11 --sign --pin 648219 --mechanism ECDSA -i data.sha1 -o data.sig --signature-format openssl
Using slot 0 with a present token (0x0)
Using signature algorithm ECDSA
```
To verify the signature:
```
-$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
+$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
Signature Verified Successfully
```
@@ -143,6 +143,6 @@ Using signature algorithm ECDSA-SHA256
The signature is verified with the hash:
```
-$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
+$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
Signature Verified Successfully
```
diff --git a/doc/store_data.md b/doc/store_data.md
index 66b1d21..eb5a8f9 100644
--- a/doc/store_data.md
+++ b/doc/store_data.md
@@ -9,7 +9,7 @@ Before writting a file into the Pico HSM, we generate the data file with the fol
```
$ echo 'Pico HSM is awesome!' > test
-```
+```
Then, we can store the data file with the following command:
@@ -43,7 +43,7 @@ Always provide a unique `--label`, as it will be used to index and reference the
To view the stored file, we can use the following command with the same label we employed:
```
-$ pkcs11-tool --read-object --type data --label 'test1'
+$ pkcs11-tool --read-object --type data --label 'test1'
Using slot 0 with a present token (0x0)
Pico HSM is awesome!
```
@@ -98,7 +98,7 @@ Data object 'test1'
applicationName: test1
Path: e82b0601040181c31f0201::cf00
Data (21 bytes): 5069636F2048534D20697320617765736F6D65210A
-
+
Data object 'test2'
applicationName: test2
Path: e82b0601040181c31f0201::cd01
diff --git a/doc/usage.md b/doc/usage.md
index e06e776..a4d65e4 100644
--- a/doc/usage.md
+++ b/doc/usage.md
@@ -1,7 +1,7 @@
# Usage
## Tools
-We use multiple tools and PKCS#11 drivers and modules, depending on the purpose.
+We use multiple tools and PKCS#11 drivers and modules, depending on the purpose.
* **pkcs11-tool**: from OpenSC. It interfaces with the HSM via PKCS#11 interface. It supports different drivers and modules.
* **sc-tool**: an alias of pkcs11-tool with the sc-hsm-embedded module. It is mainly used for AES management and it is defined as:
```
@@ -32,10 +32,10 @@ The first step is to initialize the HSM:
```
$ sc-hsm-tool --initialize --so-pin 3537363231383830 --pin 648219
```
-The PIN number is used to manage all private keys in the device. It supports three attemps. After the third PIN failure, it gets blocked.
+The PIN number is used to manage all private keys in the device. It supports three attemps. After the third PIN failure, it gets blocked.
The PIN accepts from 6 to 16 characters.
-The SO-PIN is used to unblock the PIN. It accepts 15 attemps. After 15 failed attempts, the device will be completely blocked and will be necessary to initialize again, erasing all private keys and losing the access. Therefore, keep the SO-PIN in a safe place.
+The SO-PIN is used to unblock the PIN. It accepts 15 attemps. After 15 failed attempts, the device will be completely blocked and will be necessary to initialize again, erasing all private keys and losing the access. Therefore, keep the SO-PIN in a safe place.
The SO-PIN is always 16 hexadecimal characters.
## PIN and SO-PIN management
@@ -62,7 +62,7 @@ To generate a RSA 2048 bits, use the following command:
$ pkcs11-tool -l --pin 648219 --keypairgen --key-type rsa:2048 --id 1 --label "RSA2K"
Using slot 0 with a present token (0x0)
Key pair generated:
-Private Key Object; RSA
+Private Key Object; RSA
label: RSA2K
ID: 1
Usage: decrypt, sign
@@ -77,7 +77,7 @@ The ID parameter is an internal hexadecimal number for easy identification. The
Pico HSM accepts RSA of 1024 (`rsa:1024`), 2048 (`rsa:2048`) and 4096 bits (`rsa:4096`).
-**Caution**: RSA 2048 bits may take more than 20 seconds. RSA 4096 bits may take more than 20 minutes. The Pico HSM will work as normally and neither the HSM nor the host will block. But, in the meantime, the Pico HSM will not accept any command.
+**Caution**: RSA 2048 bits may take more than 20 seconds. RSA 4096 bits may take more than 20 minutes. The Pico HSM will work as normally and neither the HSM nor the host will block. But, in the meantime, the Pico HSM will not accept any command.
An alternative is to generate the private key locally and import it to the HSM. This approach, however, is less secure as it does not use a True RNG or HRNG like Pico HSM. Use this approach if you have plugged a TRNG or you are not worried about obtaining the highest entropy.
Pico HSM also accepts ECDSA keypairs:
@@ -157,9 +157,9 @@ Certificate:
a0:30:b2:ec:d3:d6:0d:58:f3
Exponent: 65537 (0x10001)
X509v3 extensions:
- X509v3 Subject Key Identifier:
+ X509v3 Subject Key Identifier:
98:07:DA:13:B0:8E:A0:5C:97:83:68:FE:4A:25:8D:50:C4:DC:16:FA
- X509v3 Authority Key Identifier:
+ X509v3 Authority Key Identifier:
keyid:98:07:DA:13:B0:8E:A0:5C:97:83:68:FE:4A:25:8D:50:C4:DC:16:FA
X509v3 Basic Constraints: critical
@@ -173,7 +173,7 @@ Certificate:
99:2b:b2:82:66:c1:06:a7:2c:62:af:e2:e4:93:42:36:66:8d:
c5:3f:e1:ec:5f:9a:f8:5f:b3:6a:8f:0e:12:5d:c9:46:38:ea:
0b:08
-```
+```
The resulting file `cert.pem` contains the signed certificate in PEM format. Convert it into DER format and load it into the Pico HSM:
diff --git a/patch_vidpid.sh b/patch_vidpid.sh
index 0ec3ffb..ea47f29 100755
--- a/patch_vidpid.sh
+++ b/patch_vidpid.sh
@@ -1,19 +1,19 @@
#!/bin/bash
-#
+#
# This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
# Copyright (c) 2022 Pol Henarejos.
-#
-# This program is free software: you can redistribute it and/or modify
-# it under the terms of the GNU General Public License as published by
+#
+# This program is free software: you can redistribute it and/or modify
+# it under the terms of the GNU General Public License as published by
# the Free Software Foundation, version 3.
#
-# This program is distributed in the hope that it will be useful, but
-# WITHOUT ANY WARRANTY; without even the implied warranty of
-# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+# This program is distributed in the hope that it will be useful, but
+# WITHOUT ANY WARRANTY; without even the implied warranty of
+# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
# General Public License for more details.
#
-# You should have received a copy of the GNU General Public License
+# You should have received a copy of the GNU General Public License
# along with this program. If not, see .
#
diff --git a/src/hsm/cmd_challenge.c b/src/hsm/cmd_challenge.c
index 6f746b5..1fa5215 100644
--- a/src/hsm/cmd_challenge.c
+++ b/src/hsm/cmd_challenge.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/cmd_change_pin.c b/src/hsm/cmd_change_pin.c
index 874fc1e..ab57d92 100644
--- a/src/hsm/cmd_change_pin.c
+++ b/src/hsm/cmd_change_pin.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "crypto_utils.h"
#include "sc_hsm.h"
#include "kek.h"
diff --git a/src/hsm/cmd_cipher_sym.c b/src/hsm/cmd_cipher_sym.c
index 4ae4dd3..2fa7099 100644
--- a/src/hsm/cmd_cipher_sym.c
+++ b/src/hsm/cmd_cipher_sym.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/cmd_decrypt_asym.c b/src/hsm/cmd_decrypt_asym.c
index af6e0dc..147355e 100644
--- a/src/hsm/cmd_decrypt_asym.c
+++ b/src/hsm/cmd_decrypt_asym.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "common.h"
#include "mbedtls/ecdh.h"
#include "crypto_utils.h"
diff --git a/src/hsm/cmd_delete_file.c b/src/hsm/cmd_delete_file.c
index 6dd649d..3b69e78 100644
--- a/src/hsm/cmd_delete_file.c
+++ b/src/hsm/cmd_delete_file.c
@@ -1,27 +1,27 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
int cmd_delete_file() {
file_t *ef = NULL;
if (!isUserAuthenticated)
return SW_SECURITY_STATUS_NOT_SATISFIED();
-
+
if (apdu.nc == 0) {
ef = currentEF;
if (!(ef = search_dynamic_file(ef->fid)))
diff --git a/src/hsm/cmd_derive_asym.c b/src/hsm/cmd_derive_asym.c
index 907a2ec..00a8303 100644
--- a/src/hsm/cmd_derive_asym.c
+++ b/src/hsm/cmd_derive_asym.c
@@ -1,22 +1,22 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
#include "common.h"
-#include "mbedtls/ecdsa.h"
+#include "mbedtls/ecdsa.h"
#include "crypto_utils.h"
#include "sc_hsm.h"
@@ -43,7 +43,7 @@ int cmd_derive_asym() {
file_t *fkey;
if (!isUserAuthenticated)
return SW_SECURITY_STATUS_NOT_SATISFIED();
- if (!(fkey = search_dynamic_file((KEY_PREFIX << 8) | key_id)) || !fkey->data || file_get_size(fkey) == 0)
+ if (!(fkey = search_dynamic_file((KEY_PREFIX << 8) | key_id)) || !fkey->data || file_get_size(fkey) == 0)
return SW_FILE_NOT_FOUND();
if (key_has_purpose(fkey, ALGO_EC_DERIVE) == false)
return SW_CONDITIONS_NOT_SATISFIED();
@@ -52,7 +52,7 @@ int cmd_derive_asym() {
if (apdu.data[0] == ALGO_EC_DERIVE) {
mbedtls_ecdsa_context ctx;
mbedtls_ecdsa_init(&ctx);
-
+
int r;
r = load_private_key_ecdsa(&ctx, fkey);
if (r != CCID_OK) {
@@ -96,7 +96,7 @@ int cmd_derive_asym() {
mbedtls_mpi_free(&a);
mbedtls_mpi_free(&nd);
}
- else
+ else
return SW_WRONG_DATA();
return SW_OK();
}
diff --git a/src/hsm/cmd_external_authenticate.c b/src/hsm/cmd_external_authenticate.c
index 6ebfc73..df974e9 100644
--- a/src/hsm/cmd_external_authenticate.c
+++ b/src/hsm/cmd_external_authenticate.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/cmd_extras.c b/src/hsm/cmd_extras.c
index 5c1968f..440ed9b 100644
--- a/src/hsm/cmd_extras.c
+++ b/src/hsm/cmd_extras.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
#include "hardware/rtc.h"
#include "files.h"
diff --git a/src/hsm/cmd_general_authenticate.c b/src/hsm/cmd_general_authenticate.c
index 28bb876..26afc76 100644
--- a/src/hsm/cmd_general_authenticate.c
+++ b/src/hsm/cmd_general_authenticate.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -32,7 +32,7 @@ int cmd_general_authenticate() {
const uint8_t *pubkey = NULL;
uint16_t tag = 0x0;
uint8_t *tag_data = NULL, *p = NULL;
- size_t tag_len = 0;
+ size_t tag_len = 0;
while (walk_tlv(apdu.data+2, apdu.nc-2, &p, &tag, &tag_len, &tag_data)) {
if (tag == 0x80) {
pubkey = tag_data-1; //mbedtls ecdh starts reading one pos before
@@ -78,14 +78,14 @@ int cmd_general_authenticate() {
}
sm_derive_all_keys(derived, olen);
-
+
uint8_t *t = (uint8_t *)calloc(1, pubkey_len+16);
memcpy(t, "\x7F\x49\x3F\x06\x0A", 5);
if (sm_get_protocol() == MSE_AES)
memcpy(t+5, OID_ID_CA_ECDH_AES_CBC_CMAC_128, 10);
t[15] = 0x86;
memcpy(t+16, pubkey, pubkey_len);
-
+
res_APDU[res_APDU_size++] = 0x7C;
res_APDU[res_APDU_size++] = 20;
res_APDU[res_APDU_size++] = 0x81;
@@ -94,11 +94,11 @@ int cmd_general_authenticate() {
res_APDU_size += 8;
res_APDU[res_APDU_size++] = 0x82;
res_APDU[res_APDU_size++] = 8;
-
+
r = sm_sign(t, pubkey_len+16, res_APDU+res_APDU_size);
-
+
free(t);
- if (r != CCID_OK)
+ if (r != CCID_OK)
return SW_EXEC_ERROR();
res_APDU_size += 8;
}
diff --git a/src/hsm/cmd_initialize.c b/src/hsm/cmd_initialize.c
index 2a3a0de..86b4493 100644
--- a/src/hsm/cmd_initialize.c
+++ b/src/hsm/cmd_initialize.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -41,7 +41,7 @@ int cmd_initialize() {
has_session_pin = has_session_sopin = false;
uint16_t tag = 0x0;
uint8_t *tag_data = NULL, *p = NULL, *kds = NULL, *dkeks = NULL;
- size_t tag_len = 0;
+ size_t tag_len = 0;
while (walk_tlv(apdu.data, apdu.nc, &p, &tag, &tag_len, &tag_data)) {
if (tag == 0x80) { //options
file_t *tf = search_by_fid(EF_DEVOPS, NULL, SPECIFY_EF);
@@ -170,12 +170,12 @@ int cmd_initialize() {
return SW_EXEC_ERROR();
}
mbedtls_ecdsa_free(&ecdsa);
-
+
file_t *fpk = search_by_fid(EF_EE_DEV, NULL, SPECIFY_EF);
ret = flash_write_data_to_file(fpk, res_APDU, cvc_len);
if (ret != 0)
return SW_EXEC_ERROR();
-
+
const uint8_t *keyid = (const uint8_t *)"\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0\x0", *label = (const uint8_t *)"ESTERMHSM";
size_t prkd_len = asn1_build_prkd_ecc(label, strlen((const char *)label), keyid, 20, 192, res_APDU, 4096);
fpk = search_by_fid(EF_PRKD_DEV, NULL, SPECIFY_EF);
diff --git a/src/hsm/cmd_key_domain.c b/src/hsm/cmd_key_domain.c
index ee6d655..ce273be 100644
--- a/src/hsm/cmd_key_domain.c
+++ b/src/hsm/cmd_key_domain.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -120,9 +120,9 @@ int cmd_key_domain() {
if (!t86 || t86[0] != 0x4)
return SW_EXEC_ERROR();
size_t t54_len = 0;
- const uint8_t *t54 = cvc_get_field(apdu.data, apdu.nc, &t54_len, 0x54);
+ const uint8_t *t54 = cvc_get_field(apdu.data, apdu.nc, &t54_len, 0x54);
if (!t54)
- return SW_WRONG_DATA();
+ return SW_WRONG_DATA();
uint8_t hash[32], *input = (uint8_t *)calloc(1, (t86_len-1)/2+1);
input[0] = 0x54;
memcpy(input+1, t86+1, (t86_len-1)/2);
@@ -134,7 +134,7 @@ int cmd_key_domain() {
file_t *tf = file_new(EF_XKEK+p2);
if (!tf)
return SW_MEMORY_FAILURE();
-
+
//All checks done. Get Key Domain UID
pub = cvc_get_pub(apdu.data, apdu.nc, &pub_len);
if (pub) {
diff --git a/src/hsm/cmd_key_gen.c b/src/hsm/cmd_key_gen.c
index 2d3725d..949ddb6 100644
--- a/src/hsm/cmd_key_gen.c
+++ b/src/hsm/cmd_key_gen.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "crypto_utils.h"
#include "sc_hsm.h"
#include "random.h"
diff --git a/src/hsm/cmd_key_unwrap.c b/src/hsm/cmd_key_unwrap.c
index fa2070d..c541f2e 100644
--- a/src/hsm/cmd_key_unwrap.c
+++ b/src/hsm/cmd_key_unwrap.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "crypto_utils.h"
#include "sc_hsm.h"
#include "kek.h"
diff --git a/src/hsm/cmd_key_wrap.c b/src/hsm/cmd_key_wrap.c
index 0dac018..5c21faf 100644
--- a/src/hsm/cmd_key_wrap.c
+++ b/src/hsm/cmd_key_wrap.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -71,7 +71,7 @@ int cmd_key_wrap() {
uint8_t kdata[32]; //maximum AES key size
if (wait_button() == true) //timeout
return SW_SECURE_MESSAGE_EXEC_ERROR();
-
+
int key_size = file_get_size(ef), aes_type = HSM_KEY_AES;
memcpy(kdata, file_get_data(ef), key_size);
if (mkek_decrypt(kdata, key_size) != 0) {
diff --git a/src/hsm/cmd_keypair_gen.c b/src/hsm/cmd_keypair_gen.c
index fe776ee..82f3758 100644
--- a/src/hsm/cmd_keypair_gen.c
+++ b/src/hsm/cmd_keypair_gen.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "crypto_utils.h"
#include "sc_hsm.h"
#include "files.h"
@@ -29,7 +29,7 @@ int cmd_keypair_gen() {
if (!isUserAuthenticated)
return SW_SECURITY_STATUS_NOT_SATISFIED();
int ret = 0;
-
+
size_t tout = 0;
//sc_asn1_print_tags(apdu.data, apdu.nc);
uint8_t *p = NULL;
@@ -72,7 +72,7 @@ int cmd_keypair_gen() {
mbedtls_rsa_free(&rsa);
return SW_EXEC_ERROR();
}
- mbedtls_rsa_free(&rsa);
+ mbedtls_rsa_free(&rsa);
}
else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_256,MIN(oid_len,10)) == 0) { //ECC
size_t prime_len;
@@ -131,7 +131,7 @@ int cmd_keypair_gen() {
}
mbedtls_ecdsa_free(&ecdsa);
}
-
+
}
}
else
diff --git a/src/hsm/cmd_list_keys.c b/src/hsm/cmd_list_keys.c
index 84a587f..ea59704 100644
--- a/src/hsm/cmd_list_keys.c
+++ b/src/hsm/cmd_list_keys.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -48,7 +48,7 @@ int cmd_list_keys()
res_APDU[res_APDU_size++] = f->fid & 0xff;
}
}
-
+
for (int i = 0; i < dynamic_files; i++) {
file_t *f = &dynamic_file[i];
if ((f->fid & 0xff00) == (DCOD_PREFIX << 8)) {
diff --git a/src/hsm/cmd_mse.c b/src/hsm/cmd_mse.c
index f3f5e78..c1aa8e4 100644
--- a/src/hsm/cmd_mse.c
+++ b/src/hsm/cmd_mse.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -32,7 +32,7 @@ int cmd_mse() {
if (p1 & 0x1) { //SET
uint16_t tag = 0x0;
uint8_t *tag_data = NULL, *p = NULL;
- size_t tag_len = 0;
+ size_t tag_len = 0;
while (walk_tlv(apdu.data, apdu.nc, &p, &tag, &tag_len, &tag_data)) {
if (tag == 0x80) {
if (p2 == 0xA4) {
@@ -42,7 +42,7 @@ int cmd_mse() {
}
else if (tag == 0x83) {
if (tag_len == 1) {
-
+
}
else {
if (p2 == 0xB6) {
diff --git a/src/hsm/cmd_pso.c b/src/hsm/cmd_pso.c
index 8318b95..48be4fb 100644
--- a/src/hsm/cmd_pso.c
+++ b/src/hsm/cmd_pso.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
#include "oid.h"
#include "asn1.h"
@@ -53,7 +53,7 @@ int cmd_pso() {
flash_write_data_to_file(ca_ef, apdu.data, apdu.nc);
if (add_cert_puk_store(file_get_data(ca_ef), file_get_size(ca_ef), false) != CCID_OK)
return SW_FILE_FULL();
-
+
size_t chr_len = 0;
const uint8_t *chr = cvc_get_chr(apdu.data, apdu.nc, &chr_len);
if (chr == NULL)
diff --git a/src/hsm/cmd_puk_auth.c b/src/hsm/cmd_puk_auth.c
index f3e5e3d..48472b3 100644
--- a/src/hsm/cmd_puk_auth.c
+++ b/src/hsm/cmd_puk_auth.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
#include "files.h"
#include "cvc.h"
diff --git a/src/hsm/cmd_read_binary.c b/src/hsm/cmd_read_binary.c
index f32b79b..48e2af8 100644
--- a/src/hsm/cmd_read_binary.c
+++ b/src/hsm/cmd_read_binary.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -22,7 +22,7 @@ int cmd_read_binary() {
uint32_t offset = 0;
uint8_t ins = INS(apdu), p1 = P1(apdu), p2 = P2(apdu);
const file_t *ef = NULL;
-
+
if ((ins & 0x1) == 0)
{
if ((p1 & 0x80) != 0) {
@@ -39,23 +39,23 @@ int cmd_read_binary() {
if (p1 == 0 && (p2 & 0xE0) == 0 && (p2 & 0x1f) != 0 && (p2 & 0x1f) != 0x1f) {
if (!(ef = search_by_fid(p2&0x1f, NULL, SPECIFY_EF)))
return SW_FILE_NOT_FOUND ();
- }
+ }
else {
uint16_t file_id = make_uint16_t(p1, p2); // & 0x7fff;
if (file_id == 0x0)
ef = currentEF;
else if (!(ef = search_by_fid(file_id, NULL, SPECIFY_EF)) && !(ef = search_dynamic_file(file_id)))
return SW_FILE_NOT_FOUND ();
-
+
if (apdu.data[0] != 0x54)
return SW_WRONG_DATA();
-
+
offset = 0;
for (int d = 0; d < apdu.data[1]; d++)
offset |= apdu.data[2+d]<<(apdu.data[1]-1-d)*8;
- }
+ }
}
-
+
if ((fid >> 8) == KEY_PREFIX || !authenticate_action(ef, ACL_OP_READ_SEARCH)) {
return SW_SECURITY_STATUS_NOT_SATISFIED();
}
@@ -77,7 +77,7 @@ int cmd_read_binary() {
uint16_t data_len = file_get_size(ef);
if (offset > data_len)
return SW_WRONG_P1P2();
-
+
uint16_t maxle = data_len-offset;
if (apdu.ne > maxle)
apdu.ne = maxle;
diff --git a/src/hsm/cmd_reset_retry.c b/src/hsm/cmd_reset_retry.c
index 4dff5f6..cb4a678 100644
--- a/src/hsm/cmd_reset_retry.c
+++ b/src/hsm/cmd_reset_retry.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -21,7 +21,7 @@
int cmd_reset_retry() {
if (P2(apdu) != 0x81)
- return SW_REFERENCE_NOT_FOUND();
+ return SW_REFERENCE_NOT_FOUND();
if (!file_sopin || !file_pin1) {
return SW_FILE_NOT_FOUND();
}
@@ -43,7 +43,7 @@ int cmd_reset_retry() {
has_session_sopin = true;
hash_multi(apdu.data, 8, session_sopin);
}
- else if (P1(apdu) == 0x2) {
+ else if (P1(apdu) == 0x2) {
if (!has_session_sopin)
return SW_CONDITIONS_NOT_SATISFIED();
if (apdu.nc > 16)
@@ -69,7 +69,7 @@ int cmd_reset_retry() {
low_flash_available();
return SW_OK();
}
- else if (P1(apdu) == 0x1 || P1(apdu) == 0x3) {
+ else if (P1(apdu) == 0x1 || P1(apdu) == 0x3) {
if (!(opts & HSM_OPT_RRC_RESET_ONLY))
return SW_COMMAND_NOT_ALLOWED();
if (P1(apdu) == 0x1) {
diff --git a/src/hsm/cmd_select.c b/src/hsm/cmd_select.c
index b966056..e9eaa6c 100644
--- a/src/hsm/cmd_select.c
+++ b/src/hsm/cmd_select.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -42,26 +42,26 @@ int cmd_select() {
uint8_t p2 = P2(apdu);
file_t *pe = NULL;
uint16_t fid = 0x0;
-
- // Only "first or only occurence" supported
+
+ // Only "first or only occurence" supported
//if ((p2 & 0xF3) != 0x00) {
// return SW_INCORRECT_P1P2();
//}
-
+
if (apdu.nc >= 2)
fid = get_uint16_t(apdu.data, 0);
-
+
//if ((fid & 0xff00) == (KEY_PREFIX << 8))
// fid = (PRKD_PREFIX << 8) | (fid & 0xff);
-
+
uint8_t pfx = fid >> 8;
- if (pfx == PRKD_PREFIX ||
- pfx == CD_PREFIX ||
- pfx == CA_CERTIFICATE_PREFIX ||
- pfx == KEY_PREFIX ||
- pfx == EE_CERTIFICATE_PREFIX ||
- pfx == DCOD_PREFIX ||
- pfx == DATA_PREFIX ||
+ if (pfx == PRKD_PREFIX ||
+ pfx == CD_PREFIX ||
+ pfx == CA_CERTIFICATE_PREFIX ||
+ pfx == KEY_PREFIX ||
+ pfx == EE_CERTIFICATE_PREFIX ||
+ pfx == DCOD_PREFIX ||
+ pfx == DATA_PREFIX ||
pfx == PROT_DATA_PREFIX) {
if (!(pe = search_dynamic_file(fid)) && !(pe = search_by_fid(fid, NULL, SPECIFY_EF)))
return SW_FILE_NOT_FOUND();
@@ -98,7 +98,7 @@ int cmd_select() {
}
if (card_terminated) {
return set_res_sw(0x62, 0x85);
- }
+ }
}
else if (p1 == 0x08) { //Select from the MF - Path without the MF identifier
if (!(pe = search_by_path(apdu.data, apdu.nc, MF))) {
diff --git a/src/hsm/cmd_session_pin.c b/src/hsm/cmd_session_pin.c
index cd950f1..4f49f24 100644
--- a/src/hsm/cmd_session_pin.c
+++ b/src/hsm/cmd_session_pin.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
#include "random.h"
#include "eac.h"
@@ -23,7 +23,7 @@ int cmd_session_pin() {
if (P1(apdu) == 0x01 && P2(apdu) == 0x81) {
memcpy(sm_session_pin, random_bytes_get(8), 8);
sm_session_pin_len = 8;
-
+
memcpy(res_APDU, sm_session_pin, sm_session_pin_len);
res_APDU_size = sm_session_pin_len;
apdu.ne = sm_session_pin_len;
diff --git a/src/hsm/cmd_signature.c b/src/hsm/cmd_signature.c
index ce0328c..0aed65a 100644
--- a/src/hsm/cmd_signature.c
+++ b/src/hsm/cmd_signature.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "crypto_utils.h"
#include "sc_hsm.h"
#include "asn1.h"
@@ -94,7 +94,7 @@ int cmd_signature() {
file_t *fkey;
if (!isUserAuthenticated)
return SW_SECURITY_STATUS_NOT_SATISFIED();
- if (!(fkey = search_dynamic_file((KEY_PREFIX << 8) | key_id)) || !fkey->data || file_get_size(fkey) == 0)
+ if (!(fkey = search_dynamic_file((KEY_PREFIX << 8) | key_id)) || !fkey->data || file_get_size(fkey) == 0)
return SW_FILE_NOT_FOUND();
if (get_key_counter(fkey) == 0)
return SW_FILE_FULL();
@@ -114,7 +114,7 @@ int cmd_signature() {
if (p2 >= ALGO_RSA_RAW && p2 <= ALGO_RSA_PSS_SHA512) {
mbedtls_rsa_context ctx;
mbedtls_rsa_init(&ctx);
-
+
int r;
r = load_private_key_rsa(&ctx, fkey);
if (r != CCID_OK) {
@@ -144,15 +144,15 @@ int cmd_signature() {
asn1_find_tag(p, tout, 0x4, &hash_len, &hash);
}
if (oid && oid_len > 0) {
- if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA1, oid_len) == 0)
+ if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
- else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA224, oid_len) == 0)
+ else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA224, oid_len) == 0)
md = MBEDTLS_MD_SHA224;
- else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA256, oid_len) == 0)
+ else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA256, oid_len) == 0)
md = MBEDTLS_MD_SHA256;
- else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA384, oid_len) == 0)
+ else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA384, oid_len) == 0)
md = MBEDTLS_MD_SHA384;
- else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA512, oid_len) == 0)
+ else if (memcmp(oid, MBEDTLS_OID_DIGEST_ALG_SHA512, oid_len) == 0)
md = MBEDTLS_MD_SHA512;
}
if (p2 >= ALGO_RSA_PSS && p2 <= ALGO_RSA_PSS_SHA512) {
diff --git a/src/hsm/cmd_update_ef.c b/src/hsm/cmd_update_ef.c
index f5b61ac..55aff01 100644
--- a/src/hsm/cmd_update_ef.c
+++ b/src/hsm/cmd_update_ef.c
@@ -1,20 +1,20 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
-
+
#include "sc_hsm.h"
#include "asn1.h"
@@ -33,19 +33,19 @@ int cmd_update_ef() {
ef = currentEF;
else if (p1 != EE_CERTIFICATE_PREFIX && p1 != PRKD_PREFIX && p1 != CA_CERTIFICATE_PREFIX && p1 != CD_PREFIX && p1 != DATA_PREFIX && p1 != DCOD_PREFIX && p1 != PROT_DATA_PREFIX)
return SW_INCORRECT_P1P2();
-
+
if (ef && !authenticate_action(ef, ACL_OP_UPDATE_ERASE))
return SW_SECURITY_STATUS_NOT_SATISFIED();
-
+
uint16_t tag = 0x0;
uint8_t *tag_data = NULL, *p = NULL;
- size_t tag_len = 0;
+ size_t tag_len = 0;
while (walk_tlv(apdu.data, apdu.nc, &p, &tag, &tag_len, &tag_data)) {
if (tag == 0x54) { //ofset tag
for (int i = 1; i <= tag_len; i++)
offset |= (*tag_data++ << (8*(tag_len-i)));
}
- else if (tag == 0x53) { //data
+ else if (tag == 0x53) { //data
data_len = tag_len;
data = tag_data;
}
@@ -71,7 +71,7 @@ int cmd_update_ef() {
else {
if (!ef->data)
return SW_DATA_INVALID();
-
+
uint8_t *data_merge = (uint8_t *)calloc(1, offset+data_len);
memcpy(data_merge, file_get_data(ef), offset);
memcpy(data_merge+offset, data, data_len);
@@ -82,5 +82,5 @@ int cmd_update_ef() {
}
low_flash_available();
}
- return SW_OK();
+ return SW_OK();
}
diff --git a/src/hsm/cmd_verify.c b/src/hsm/cmd_verify.c
index 33436a9..7a21611 100644
--- a/src/hsm/cmd_verify.c
+++ b/src/hsm/cmd_verify.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -20,7 +20,7 @@
int cmd_verify() {
uint8_t p1 = P1(apdu);
uint8_t p2 = P2(apdu);
-
+
if (p1 != 0x0 || (p2 & 0x60) != 0x0)
return SW_WRONG_P1P2();
diff --git a/src/hsm/cvc.c b/src/hsm/cvc.c
index 4c00c08..f65fbed 100644
--- a/src/hsm/cvc.c
+++ b/src/hsm/cvc.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -126,7 +126,7 @@ size_t asn1_cvc_cert_body(void *rsa_ecdsa, uint8_t key_type, uint8_t *buf, size_
uint8_t *car = NULL, *chr = NULL;
size_t lencar = 0, lenchr = 0;
-
+
if (asn1_find_tag(apdu.data, apdu.nc, 0x42, &lencar, &car) == false || lencar == 0 || car == NULL) {
car = (uint8_t *)dev_name;
lencar = dev_name_len;
@@ -136,9 +136,9 @@ size_t asn1_cvc_cert_body(void *rsa_ecdsa, uint8_t key_type, uint8_t *buf, size_
lenchr = dev_name_len;
}
size_t car_size = asn1_len_tag(0x42, lencar), chr_size = asn1_len_tag(0x5f20, lenchr);
-
+
size_t tot_len = asn1_len_tag(0x7f4e, cpi_size+car_size+pubkey_size+chr_size+ext_size);
-
+
if (buf_len == 0 || buf == NULL)
return tot_len;
if (buf_len < tot_len)
@@ -283,14 +283,14 @@ size_t asn1_build_cert_description(const uint8_t *label, size_t label_len, const
*p++ = 0x3;
p += format_tlv_len(opt_len, p);
memcpy(p, "\x06\x40", 2); p += 2;
-
+
//Seq 2
*p++ = 0x30;
p += format_tlv_len(asn1_len_tag(0x4, 20), p);
*p++ = 0x4;
p += format_tlv_len(20, p);
mbedtls_md(mbedtls_md_info_from_type(MBEDTLS_MD_SHA1), puk, puk_len, p); p += 20;
-
+
//Seq 3
*p++ = 0xA1;
p += format_tlv_len(asn1_len_tag(0x30, asn1_len_tag(0x30, asn1_len_tag(0x4, sizeof(uint16_t)))), p);
@@ -323,7 +323,7 @@ size_t asn1_build_prkd_ecc(const uint8_t *label, size_t label_len, const uint8_t
*p++ = 0xC;
p += format_tlv_len(label_len, p);
memcpy(p, label, label_len); p += label_len;
-
+
//Seq 2
*p++ = 0x30;
p += format_tlv_len(asn1_len_tag(0x4, keyid_len)+asn1_len_tag(0x3, 3), p);
@@ -333,7 +333,7 @@ size_t asn1_build_prkd_ecc(const uint8_t *label, size_t label_len, const uint8_t
*p++ = 0x3;
p += format_tlv_len(3, p);
memcpy(p, "\x07\x20\x80", 3); p += 3;
-
+
//Seq 3
*p++ = 0xA1;
p += format_tlv_len(asn1_len_tag(0x30, asn1_len_tag(0x30, asn1_len_tag(0x4, 0))+asn1_len_tag(0x2,2)), p);
@@ -444,7 +444,7 @@ mbedtls_ecp_group_id cvc_inherite_ec_group(const uint8_t *ca, size_t ca_len) {
const uint8_t *t81 = cvc_get_field(ca_puk, ca_puk_len, &t81_len, 0x81);
if (!t81)
return MBEDTLS_ECP_DP_NONE;
-
+
return ec_get_curve_from_prime(t81, t81_len);
}
@@ -465,11 +465,11 @@ int puk_verify(const uint8_t *sig, size_t sig_len, const uint8_t *hash, size_t h
mbedtls_rsa_context rsa;
mbedtls_rsa_init(&rsa);
mbedtls_md_type_t md = MBEDTLS_MD_NONE;
- if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_1, oid_len) == 0)
+ if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
- else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_256, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_256, oid_len) == 0)
md = MBEDTLS_MD_SHA256;
- else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_512, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_512, oid_len) == 0)
md = MBEDTLS_MD_SHA512;
else if (memcmp(oid, OID_ID_TA_RSA_PSS_SHA_1, oid_len) == 0) {
md = MBEDTLS_MD_SHA1;
@@ -514,19 +514,19 @@ int puk_verify(const uint8_t *sig, size_t sig_len, const uint8_t *hash, size_t h
}
else if (memcmp(oid, OID_ID_TA_ECDSA, 9) == 0) { //ECC
mbedtls_md_type_t md = MBEDTLS_MD_NONE;
- if (memcmp(oid, OID_ID_TA_ECDSA_SHA_1, oid_len) == 0)
+ if (memcmp(oid, OID_ID_TA_ECDSA_SHA_1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_224, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_224, oid_len) == 0)
md = MBEDTLS_MD_SHA224;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_256, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_256, oid_len) == 0)
md = MBEDTLS_MD_SHA256;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_384, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_384, oid_len) == 0)
md = MBEDTLS_MD_SHA384;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_512, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_512, oid_len) == 0)
md = MBEDTLS_MD_SHA512;
- if (md == MBEDTLS_MD_NONE)
+ if (md == MBEDTLS_MD_NONE)
return CCID_WRONG_DATA;
-
+
size_t t86_len = 0;
const uint8_t *t86 = cvc_get_field(puk, puk_len, &t86_len, 0x86);
if (!t86)
@@ -595,11 +595,11 @@ int cvc_verify(const uint8_t *cert, size_t cert_len, const uint8_t *ca, size_t c
return CCID_WRONG_DATA;
mbedtls_md_type_t md = MBEDTLS_MD_NONE;
if (memcmp(oid, OID_ID_TA_RSA, 9) == 0) { //RSA
- if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_1, oid_len) == 0)
+ if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
- else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_256, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_256, oid_len) == 0)
md = MBEDTLS_MD_SHA256;
- else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_512, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_RSA_V1_5_SHA_512, oid_len) == 0)
md = MBEDTLS_MD_SHA512;
else if (memcmp(oid, OID_ID_TA_RSA_PSS_SHA_1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
@@ -609,18 +609,18 @@ int cvc_verify(const uint8_t *cert, size_t cert_len, const uint8_t *ca, size_t c
md = MBEDTLS_MD_SHA512;
}
else if (memcmp(oid, OID_ID_TA_ECDSA, 9) == 0) { //ECC
- if (memcmp(oid, OID_ID_TA_ECDSA_SHA_1, oid_len) == 0)
+ if (memcmp(oid, OID_ID_TA_ECDSA_SHA_1, oid_len) == 0)
md = MBEDTLS_MD_SHA1;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_224, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_224, oid_len) == 0)
md = MBEDTLS_MD_SHA224;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_256, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_256, oid_len) == 0)
md = MBEDTLS_MD_SHA256;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_384, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_384, oid_len) == 0)
md = MBEDTLS_MD_SHA384;
- else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_512, oid_len) == 0)
+ else if (memcmp(oid, OID_ID_TA_ECDSA_SHA_512, oid_len) == 0)
md = MBEDTLS_MD_SHA512;
}
- if (md == MBEDTLS_MD_NONE)
+ if (md == MBEDTLS_MD_NONE)
return CCID_WRONG_DATA;
const mbedtls_md_info_t *md_info = mbedtls_md_info_from_type(md);
uint8_t hash[64], hash_len = mbedtls_md_get_size(md_info);
diff --git a/src/hsm/cvc.h b/src/hsm/cvc.h
index 90c2774..c5babfe 100644
--- a/src/hsm/cvc.h
+++ b/src/hsm/cvc.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/files.c b/src/hsm/files.c
index d1d7eb8..a00bdf6 100644
--- a/src/hsm/files.c
+++ b/src/hsm/files.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/files.h b/src/hsm/files.h
index 0b8d772..6090d55 100644
--- a/src/hsm/files.h
+++ b/src/hsm/files.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/kek.c b/src/hsm/kek.c
index 0a06655..8af6bf3 100644
--- a/src/hsm/kek.c
+++ b/src/hsm/kek.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -215,7 +215,7 @@ int mkek_decrypt(uint8_t *data, size_t len) {
int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_t *out_len, const uint8_t *allowed, size_t allowed_len) {
if (!(key_type & HSM_KEY_RSA) && !(key_type & HSM_KEY_EC) && !(key_type & HSM_KEY_AES))
return CCID_WRONG_DATA;
-
+
uint8_t kb[8+2*4+2*4096/8+3+13]; //worst case: RSA-4096 (plus, 13 bytes padding)
memset(kb, 0, sizeof(kb));
int kb_len = 0, r = 0;
@@ -226,19 +226,19 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
r = dkek_kenc(id, kenc);
if (r != CCID_OK)
return r;
-
+
uint8_t kcv[8];
memset(kcv, 0, sizeof(kcv));
r = dkek_kcv(id, kcv);
if (r != CCID_OK)
return r;
-
+
uint8_t kmac[32];
memset(kmac, 0, sizeof(kmac));
r = dkek_kmac(id, kmac);
if (r != CCID_OK)
return r;
-
+
if (key_type & HSM_KEY_AES) {
if (key_type & HSM_KEY_AES_128)
kb_len = 16;
@@ -246,38 +246,38 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
kb_len = 24;
else if (key_type & HSM_KEY_AES_256)
kb_len = 32;
-
+
if (kb_len != 16 && kb_len != 24 && kb_len != 32)
return CCID_WRONG_DATA;
if (*out_len < 8+1+10+6+4+(2+32+14)+16)
return CCID_WRONG_LENGTH;
-
+
put_uint16_t(kb_len, kb+8);
memcpy(kb+10, key_ctx, kb_len);
kb_len += 2;
-
+
algo = (uint8_t *)"\x00\x08\x60\x86\x48\x01\x65\x03\x04\x01"; //2.16.840.1.101.3.4.1 (2+8)
algo_len = 10;
}
else if (key_type & HSM_KEY_RSA) {
- if (*out_len < 8+1+12+6+(8+2*4+2*4096/8+3+13)+16) //13 bytes pading
+ if (*out_len < 8+1+12+6+(8+2*4+2*4096/8+3+13)+16) //13 bytes pading
return CCID_WRONG_LENGTH;
mbedtls_rsa_context *rsa = (mbedtls_rsa_context *)key_ctx;
kb_len = 0;
put_uint16_t(mbedtls_rsa_get_len(rsa)*8, kb+8+kb_len); kb_len += 2;
-
+
put_uint16_t(mbedtls_mpi_size(&rsa->D), kb+8+kb_len); kb_len += 2;
mbedtls_mpi_write_binary(&rsa->D, kb+8+kb_len, mbedtls_mpi_size(&rsa->D)); kb_len += mbedtls_mpi_size(&rsa->D);
put_uint16_t(mbedtls_mpi_size(&rsa->N), kb+8+kb_len); kb_len += 2;
mbedtls_mpi_write_binary(&rsa->N, kb+8+kb_len, mbedtls_mpi_size(&rsa->N)); kb_len += mbedtls_mpi_size(&rsa->N);
put_uint16_t(mbedtls_mpi_size(&rsa->E), kb+8+kb_len); kb_len += 2;
mbedtls_mpi_write_binary(&rsa->E, kb+8+kb_len, mbedtls_mpi_size(&rsa->E)); kb_len += mbedtls_mpi_size(&rsa->E);
-
+
algo = (uint8_t *)"\x00\x0A\x04\x00\x7F\x00\x07\x02\x02\x02\x01\x02";
algo_len = 12;
}
else if (key_type & HSM_KEY_EC) {
- if (*out_len < 8+1+12+6+(8+2*8+9*66+2+4)+16) //4 bytes pading
+ if (*out_len < 8+1+12+6+(8+2*8+9*66+2+4)+16) //4 bytes pading
return CCID_WRONG_LENGTH;
mbedtls_ecdsa_context *ecdsa = (mbedtls_ecdsa_context *)key_ctx;
kb_len = 0;
@@ -300,16 +300,16 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
kb[8+kb_len++] = 0x4;
mbedtls_mpi_write_binary(&ecdsa->Q.X, kb+8+kb_len, mbedtls_mpi_size(&ecdsa->Q.X)); kb_len += mbedtls_mpi_size(&ecdsa->Q.X);
mbedtls_mpi_write_binary(&ecdsa->Q.Y, kb+8+kb_len, mbedtls_mpi_size(&ecdsa->Q.Y)); kb_len += mbedtls_mpi_size(&ecdsa->Q.Y);
-
+
algo = (uint8_t *)"\x00\x0A\x04\x00\x7F\x00\x07\x02\x02\x02\x02\x03";
algo_len = 12;
}
memset(out, 0, *out_len);
*out_len = 0;
-
+
memcpy(out+*out_len, kcv, 8);
*out_len += 8;
-
+
if (key_type & HSM_KEY_AES)
out[*out_len] = 15;
else if (key_type & HSM_KEY_RSA)
@@ -317,14 +317,14 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
else if (key_type & HSM_KEY_EC)
out[*out_len] = 12;
*out_len += 1;
-
+
if (algo) {
memcpy(out+*out_len, algo, algo_len);
*out_len += algo_len;
}
else
*out_len += 2;
-
+
if (allowed && allowed_len > 0) {
put_uint16_t(allowed_len, out+*out_len); *out_len += 2;
memcpy(out+*out_len, allowed, allowed_len);
@@ -334,7 +334,7 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
*out_len += 2;
//add 4 zeros
*out_len += 4;
-
+
memcpy(kb, random_bytes_get(8), 8);
kb_len += 8; //8 random bytes
int kb_len_pad = ((int)(kb_len/16))*16;
@@ -347,12 +347,12 @@ int dkek_encode_key(uint8_t id, void *key_ctx, int key_type, uint8_t *out, size_
r = aes_encrypt(kenc, NULL, 256, HSM_AES_MODE_CBC, kb, kb_len_pad);
if (r != CCID_OK)
return r;
-
+
memcpy(out+*out_len, kb, kb_len_pad);
*out_len += kb_len_pad;
r = mbedtls_cipher_cmac(mbedtls_cipher_info_from_type(MBEDTLS_CIPHER_AES_256_ECB), kmac, 256, out, *out_len, out+*out_len);
-
+
*out_len += 16;
if (r != 0)
return r;
@@ -376,62 +376,62 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
r = dkek_kcv(id, kcv);
if (r != CCID_OK)
return r;
-
+
uint8_t kmac[32];
memset(kmac, 0, sizeof(kmac));
r = dkek_kmac(id, kmac);
if (r != CCID_OK)
return r;
-
+
uint8_t kenc[32];
memset(kenc, 0, sizeof(kenc));
r = dkek_kenc(id, kenc);
if (r != CCID_OK)
return r;
-
+
if (memcmp(kcv, in, 8) != 0)
return CCID_WRONG_DKEK;
-
+
uint8_t signature[16];
r = mbedtls_cipher_cmac(mbedtls_cipher_info_from_type(MBEDTLS_CIPHER_AES_256_ECB), kmac, 256, in, in_len-16, signature);
if (r != 0)
return CCID_WRONG_SIGNATURE;
if (memcmp(signature, in+in_len-16, 16) != 0)
return CCID_WRONG_SIGNATURE;
-
+
int key_type = in[8];
if (key_type != 5 && key_type != 6 && key_type != 12 && key_type != 15)
return CCID_WRONG_DATA;
-
+
if ((key_type == 5 || key_type == 6) && memcmp(in+9, "\x00\x0A\x04\x00\x7F\x00\x07\x02\x02\x02\x01\x02", 12) != 0)
return CCID_WRONG_DATA;
-
+
if (key_type == 12 && memcmp(in+9, "\x00\x0A\x04\x00\x7F\x00\x07\x02\x02\x02\x02\x03", 12) != 0)
return CCID_WRONG_DATA;
-
+
if (key_type == 15 && memcmp(in+9, "\x00\x08\x60\x86\x48\x01\x65\x03\x04\x01", 10) != 0)
return CCID_WRONG_DATA;
-
+
size_t ofs = 9;
-
+
//OID
size_t len = get_uint16_t(in, ofs);
ofs += len+2;
-
+
//Allowed algorithms
len = get_uint16_t(in, ofs);
*allowed = (uint8_t *)(in+ofs+2);
*allowed_len = len;
ofs += len+2;
-
+
//Access conditions
len = get_uint16_t(in, ofs);
ofs += len+2;
-
+
//Key OID
len = get_uint16_t(in, ofs);
ofs += len+2;
-
+
if ((in_len-16-ofs) % 16 != 0)
return CCID_WRONG_PADDING;
uint8_t kb[8+2*4+2*4096/8+3+13]; //worst case: RSA-4096 (plus, 13 bytes padding)
@@ -440,7 +440,7 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
r = aes_decrypt(kenc, NULL, 256, HSM_AES_MODE_CBC, kb, in_len-16-ofs);
if (r != CCID_OK)
return r;
-
+
int key_size = get_uint16_t(kb, 8);
if (key_size_out)
*key_size_out = key_size;
@@ -455,7 +455,7 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
mbedtls_rsa_free(rsa);
return CCID_WRONG_DATA;
}
-
+
len = get_uint16_t(kb, ofs); ofs += 2;
r = mbedtls_mpi_read_binary(&rsa->N, kb+ofs, len); ofs += len;
if (r != 0) {
@@ -466,20 +466,20 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
else if (key_type == 6) {
//DP-1
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
//DQ-1
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
len = get_uint16_t(kb, ofs); ofs += 2;
r = mbedtls_mpi_read_binary(&rsa->P, kb+ofs, len); ofs += len;
if (r != 0) {
mbedtls_rsa_free(rsa);
return CCID_WRONG_DATA;
}
-
+
//PQ
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
len = get_uint16_t(kb, ofs); ofs += 2;
r = mbedtls_mpi_read_binary(&rsa->Q, kb+ofs, len); ofs += len;
if (r != 0) {
@@ -489,14 +489,14 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
//N
len = get_uint16_t(kb, ofs); ofs += len+2;
}
-
+
len = get_uint16_t(kb, ofs); ofs += 2;
r = mbedtls_mpi_read_binary(&rsa->E, kb+ofs, len); ofs += len;
if (r != 0) {
mbedtls_rsa_free(rsa);
return CCID_WRONG_DATA;
}
-
+
if (key_type == 5) {
r = mbedtls_rsa_import(rsa, &rsa->N, NULL, NULL, &rsa->D, &rsa->E);
if (r != 0) {
@@ -511,7 +511,7 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
return CCID_EXEC_ERROR;
}
}
-
+
r = mbedtls_rsa_complete(rsa);
if (r != 0) {
mbedtls_rsa_free(rsa);
@@ -526,13 +526,13 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
else if (key_type == 12) {
mbedtls_ecdsa_context *ecdsa = (mbedtls_ecdsa_context *)key_ctx;
mbedtls_ecdsa_init(ecdsa);
-
+
//A
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
//B
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
//P
len = get_uint16_t(kb, ofs); ofs += 2;
mbedtls_ecp_group_id ec_id = ec_get_curve_from_prime(kb+ofs, len);
@@ -541,13 +541,13 @@ int dkek_decode_key(uint8_t id, void *key_ctx, const uint8_t *in, size_t in_len,
return CCID_WRONG_DATA;
}
ofs += len;
-
+
//N
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
//G
len = get_uint16_t(kb, ofs); ofs += len+2;
-
+
//d
len = get_uint16_t(kb, ofs); ofs += 2;
r = mbedtls_ecp_read_key(ec_id, ecdsa, kb+ofs, len);
diff --git a/src/hsm/kek.h b/src/hsm/kek.h
index cd18240..8a0e5d1 100644
--- a/src/hsm/kek.h
+++ b/src/hsm/kek.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/oid.c b/src/hsm/oid.c
index 56d2da0..f7395c2 100644
--- a/src/hsm/oid.c
+++ b/src/hsm/oid.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/oid.h b/src/hsm/oid.h
index e758f7c..c59063f 100644
--- a/src/hsm/oid.h
+++ b/src/hsm/oid.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -70,7 +70,7 @@
#define OID_ID_RI_DH_SHA_224 OID_ID_RI_DH "\x02"
#define OID_ID_RI_DH_SHA_256 OID_ID_RI_DH "\x03"
-#define OID_ID_RI_ECDH OID_ID_RI "\x02"
+#define OID_ID_RI_ECDH OID_ID_RI "\x02"
#define OID_ID_RI_ECDH_SHA_1 OID_ID_RI_ECDH "\x01"
#define OID_ID_RI_ECDH_SHA_224 OID_ID_RI_ECDH "\x02"
diff --git a/src/hsm/sc_hsm.c b/src/hsm/sc_hsm.c
index 803ffb9..de25bdb 100644
--- a/src/hsm/sc_hsm.c
+++ b/src/hsm/sc_hsm.c
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
@@ -26,13 +26,13 @@
#include "asn1.h"
const uint8_t sc_hsm_aid[] = {
- 11,
+ 11,
0xE8,0x2B,0x06,0x01,0x04,0x01,0x81,0xC3,0x1F,0x02,0x01
};
-const uint8_t atr_sc_hsm[] = {
+const uint8_t atr_sc_hsm[] = {
24,
- 0x3B,0xFE,0x18,0x00,0x00,0x81,0x31,0xFE,0x45,0x80,0x31,0x81,0x54,0x48,0x53,0x4D,0x31,0x73,0x80,0x21,0x40,0x81,0x07,0xFA
+ 0x3B,0xFE,0x18,0x00,0x00,0x81,0x31,0xFE,0x45,0x80,0x31,0x81,0x54,0x48,0x53,0x4D,0x31,0x73,0x80,0x21,0x40,0x81,0x07,0xFA
};
uint8_t session_pin[32], session_sopin[32];
@@ -84,7 +84,7 @@ app_t *sc_hsm_select_aid(app_t *a) {
return NULL;
}
-void __attribute__ ((constructor)) sc_hsm_ctor() {
+void __attribute__ ((constructor)) sc_hsm_ctor() {
ccid_atr = atr_sc_hsm;
register_app(sc_hsm_select_aid);
}
@@ -135,7 +135,7 @@ void scan_files() {
printf("FATAL ERROR: Retries SOPIN not found in memory!\r\n");
}
file_t *tf = NULL;
-
+
tf = search_by_fid(0x1082, NULL, SPECIFY_EF);
if (tf) {
if (!tf->data) {
@@ -176,7 +176,7 @@ int add_cert_puk_store(const uint8_t *data, size_t data_len, bool copy) {
return CCID_ERR_NULL_PARAM;
if (puk_store_entries == MAX_PUK_STORE_ENTRIES)
return CCID_ERR_MEMORY_FATAL;
-
+
puk_store[puk_store_entries].copied = copy;
if (copy == true) {
uint8_t *tmp = (uint8_t *)calloc(data_len, sizeof(uint8_t));
@@ -189,7 +189,7 @@ int add_cert_puk_store(const uint8_t *data, size_t data_len, bool copy) {
puk_store[puk_store_entries].chr = cvc_get_chr(puk_store[puk_store_entries].cvcert, data_len, &puk_store[puk_store_entries].chr_len);
puk_store[puk_store_entries].car = cvc_get_car(puk_store[puk_store_entries].cvcert, data_len, &puk_store[puk_store_entries].car_len);
puk_store[puk_store_entries].puk = cvc_get_pub(puk_store[puk_store_entries].cvcert, data_len, &puk_store[puk_store_entries].puk_len);
-
+
puk_store_entries++;
return CCID_OK;
}
@@ -278,7 +278,7 @@ int parse_token_info(const file_t *f, int mode) {
int pin_reset_retries(const file_t *pin, bool force) {
if (!pin)
- return CCID_ERR_NULL_PARAM;
+ return CCID_ERR_NULL_PARAM;
const file_t *max = search_by_fid(pin->fid+1, NULL, SPECIFY_EF);
const file_t *act = search_by_fid(pin->fid+2, NULL, SPECIFY_EF);
if (!max || !act)
@@ -294,7 +294,7 @@ int pin_reset_retries(const file_t *pin, bool force) {
int pin_wrong_retry(const file_t *pin) {
if (!pin)
- return CCID_ERR_NULL_PARAM;
+ return CCID_ERR_NULL_PARAM;
const file_t *act = search_by_fid(pin->fid+2, NULL, SPECIFY_EF);
if (!act)
return CCID_ERR_FILE_NOT_FOUND;
@@ -381,7 +381,7 @@ uint32_t get_key_counter(file_t *fkey) {
const uint8_t *meta_tag = get_meta_tag(fkey, 0x90, &tag_len);
if (meta_tag)
return (meta_tag[0] << 24) | (meta_tag[1] << 16) | (meta_tag[2] << 8) | meta_tag[3];
- return 0xffffffff;
+ return 0xffffffff;
}
bool key_has_purpose(file_t *ef, uint8_t purpose) {
@@ -417,7 +417,7 @@ uint32_t decrement_key_counter(file_t *fkey) {
tag_data[1] = (val >> 16) & 0xff;
tag_data[2] = (val >> 8) & 0xff;
tag_data[3] = val & 0xff;
-
+
int r = meta_add(fkey->fid, cmeta, meta_size);
free(cmeta);
if (r != 0)
@@ -525,7 +525,7 @@ int find_and_store_meta_key(uint8_t key_id) {
int load_private_key_rsa(mbedtls_rsa_context *ctx, file_t *fkey) {
if (wait_button() == true) //timeout
return CCID_VERIFICATION_FAILED;
-
+
int key_size = file_get_size(fkey);
uint8_t kdata[4096/8];
memcpy(kdata, file_get_data(fkey), key_size);
@@ -568,7 +568,7 @@ int load_private_key_rsa(mbedtls_rsa_context *ctx, file_t *fkey) {
int load_private_key_ecdsa(mbedtls_ecdsa_context *ctx, file_t *fkey) {
if (wait_button() == true) //timeout
return CCID_VERIFICATION_FAILED;
-
+
int key_size = file_get_size(fkey);
uint8_t kdata[67]; //Worst case, 521 bit + 1byte
memcpy(kdata, file_get_data(fkey), key_size);
@@ -622,7 +622,7 @@ typedef struct cmd
static const cmd_t cmds[] = {
{ INS_SELECT_FILE, cmd_select },
- { INS_LIST_KEYS, cmd_list_keys },
+ { INS_LIST_KEYS, cmd_list_keys },
{ INS_READ_BINARY, cmd_read_binary },
{ INS_READ_BINARY_ODD, cmd_read_binary },
{ INS_VERIFY, cmd_verify },
diff --git a/src/hsm/sc_hsm.h b/src/hsm/sc_hsm.h
index a031f77..98391f8 100644
--- a/src/hsm/sc_hsm.h
+++ b/src/hsm/sc_hsm.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/src/hsm/version.h b/src/hsm/version.h
index 5e0421a..792e9af 100644
--- a/src/hsm/version.h
+++ b/src/hsm/version.h
@@ -1,17 +1,17 @@
-/*
+/*
* This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
* Copyright (c) 2022 Pol Henarejos.
- *
- * This program is free software: you can redistribute it and/or modify
- * it under the terms of the GNU General Public License as published by
+ *
+ * This program is free software: you can redistribute it and/or modify
+ * it under the terms of the GNU General Public License as published by
* the Free Software Foundation, version 3.
*
- * This program is distributed in the hope that it will be useful, but
- * WITHOUT ANY WARRANTY; without even the implied warranty of
- * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+ * This program is distributed in the hope that it will be useful, but
+ * WITHOUT ANY WARRANTY; without even the implied warranty of
+ * MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
* General Public License for more details.
*
- * You should have received a copy of the GNU General Public License
+ * You should have received a copy of the GNU General Public License
* along with this program. If not, see .
*/
diff --git a/workflows/autobuild.sh b/workflows/autobuild.sh
index eb65ec6..09ef1c7 100755
--- a/workflows/autobuild.sh
+++ b/workflows/autobuild.sh
@@ -10,4 +10,4 @@ cd ..
mkdir build
cd build
cmake -DPICO_SDK_PATH=../pico-sdk ..
-make
+make
 -Once finished, export the public key.
+Once finished, export the public key.
-Once finished, export the public key.
+Once finished, export the public key.
 @@ -64,17 +64,17 @@ From now on, you have full access and can operate normally with the primary devi
Pico HSM uses the PIN to protect the DKEK, which is lately used to protect private/secret keys and wrap/unwrap. However, when PKA is enabled, the authentication is not performed by introducing any PIN.
Authenticated privileges are granted when PKA succeeds, regardless of PIN, which is optional.
-Nevertheless, **it is extremely recommended to combine PKA with PIN**. Note that when combined, only PKA grants authenticated privileges. Therefore, if both schemes are setup, it is necessary to unlock the DKEK with PIN verification.
+Nevertheless, **it is extremely recommended to combine PKA with PIN**. Note that when combined, only PKA grants authenticated privileges. Therefore, if both schemes are setup, it is necessary to unlock the DKEK with PIN verification.
Otherwise, it will not be possible to operate with private/secret keys despite the user will be logged in.
With this scheme, multiple custodians may authenticate the device individually and remotely and, when fully authenticated, the master user can unlock the DKEK with the PIN.
-Moreover, with this approach the device is kept safe and neither the DKEK nor the private/secret keys are stored in plain text in the device.
+Moreover, with this approach the device is kept safe and neither the DKEK nor the private/secret keys are stored in plain text in the device.
Even though the flash memory is dumped by an attacker, it will not be possible to decipher any sensitive data or key.
Initialization of the device with PKA **and** PIN can be achieved with SCS3 or OpenSC:
-**Note:** do not import any DKEK share or DKEK operation before PKA and PIN setup.
+**Note:** do not import any DKEK share or DKEK operation before PKA and PIN setup.
### With OpenSC
@@ -84,9 +84,9 @@ Use the following command (or similar), which accepts the use of PIN parameter *
sc-hsm-tool -X --so-pin 1234567890123456 --pin 648219 -K 1 -n 1 -s 1
```
-and PKA and PIN are enabled, jointly with DKEK protection.
+and PKA and PIN are enabled, jointly with DKEK protection.
-### With SCS3
+###�With SCS3
Unfortunately, SCS3 does not allow to initialize the device with PKA and PIN at the same time, though it can be achieved in separated steps:
@@ -94,4 +94,4 @@ Unfortunately, SCS3 does not allow to initialize the device with PKA and PIN at
2. There is NO default PIN. So, DO NOT attempt to log in yet. A reset PIN shall be requested.
3. Click on ``Reset User-PIN``, introduce the SO-PIN configured during the initialization and introduce the desired User-PIN.
-When done, the device will be configured with PIN **and** PKA.
+When done, the device will be configured with PIN **and** PKA.
diff --git a/doc/scs3.md b/doc/scs3.md
index 92573e1..8dd9dbe 100644
--- a/doc/scs3.md
+++ b/doc/scs3.md
@@ -4,11 +4,11 @@ SCS3 tool is a specific tool developed by CardContact to manage HSM. Thanks to i
- Import PKCS12 private keys and certificates.
- Import private keys and certificates from other Pico HSM devices in WKY format.
--
+-
Unfortunately, there is no pkcs11 tool or equivalent capable to perform the import. Since it uses the SC-HSM driver, it also supports the communication with the [SCS3 tool](https://www.openscdp.org/scsh3/ "SCS3 tool"). It can be downloaded from [here](https://www.openscdp.org/scsh3/download.html "here").
-However, SCS3 only works with those HSM manufactured by CardContact. The check is performed by means of trust store against the manufacturing certificates. For obvious reasons, these certificates can only be signed with the private keys of the Certificate Authorities listed in the trust store.
+However, SCS3 only works with those HSM manufactured by CardContact. The check is performed by means of trust store against the manufacturing certificates. For obvious reasons, these certificates can only be signed with the private keys of the Certificate Authorities listed in the trust store.
Pico HSM is shipped with its own CA certificates. To load this certificate onto the trust store of SCS3, the following line has to be appended to `SmartCardHSM.rootCerts` variable, near line `235` in the file `scs3/scsh/sc-hsm/SmartCardHSM.js`.
@@ -39,8 +39,8 @@ After this ammendment, the program can be started and the KeyManager can be invo
>load("keymanager/keymanager.js");
SmartCard-HSM Version 1.6 on JCOP Free memory 217104 byte
-Issuer Certificate : CVC id-AT DV (official domestic) CAR=ESCVCAHSM00001 CHR=ESDVCAHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2025
-Device Certificate : CVC id-AT Terminal CAR=ESDVCAHSM00001 CHR=ESTERMHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2023
+Issuer Certificate : CVC id-AT DV (official domestic) CAR=ESCVCAHSM00001 CHR=ESDVCAHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2025
+Device Certificate : CVC id-AT Terminal CAR=ESDVCAHSM00001 CHR=ESTERMHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2023
Default Key Domain : 0F89B400975EDD2D425ABF85F2FBD318779B3D85475E65D4
-------------------------------------------------------------------
Please right-click on nodes in the outline to see possible actions.
@@ -60,7 +60,7 @@ It can be executed in a Terminal via
```
## DKEK requirement
-In order to perform the import, private keys must be wrapped with the same DKEK present in the Pico HSM. Thus, the Pico HSM must be previously initialized with at minimum of 1 DKEK share. This share will be used to wrap the private key before import.
+In order to perform the import, private keys must be wrapped with the same DKEK present in the Pico HSM. Thus, the Pico HSM must be previously initialized with at minimum of 1 DKEK share. This share will be used to wrap the private key before import.
Note that the DKEK share shall be available before the import. In this way, all custodians must be present during the import process, since they will have to introduce their respective DKEK.
diff --git a/doc/sign-verify.md b/doc/sign-verify.md
index 1c668e7..c7c1c93 100644
--- a/doc/sign-verify.md
+++ b/doc/sign-verify.md
@@ -1,7 +1,7 @@
# Sign and verify
Pico HSM supports in place signature of arbitrary data. It supports the following algorithms:
-* RSA-PKCS
+* RSA-PKCS
* RSA-X-509
* SHA1-RSA-PKCS
* SHA256-RSA-PKCS
@@ -32,7 +32,7 @@ $ openssl rsa -inform DER -outform PEM -in 1.der -pubin > 1.pub
At this moment, you are able to verify with the public key in `1.pub`. The signature is computed inside the Pico HSM with the private key. It never leaves the device.
## RSA-PKCS
-This algorithm is used to sign raw data.
+This algorithm is used to sign raw data.
To sign the data:
```
@@ -91,7 +91,7 @@ This algorithm uses the RSA-PKCS with PSS salt to randomize the signature. Pico
To sign the data:
```
$ pkcs11-tool --id 1 --sign --pin 648219 --mechanism RSA-PKCS-PSS -i data.sha1 -o data.sig
-```
+```
To verify the signature:
```
@@ -105,7 +105,7 @@ This algorithm takes the file as the input and sends its hash for signing with t
To sign the data:
```
$ pkcs11-tool --id 1 --sign --pin 648219 --mechanism SHA1-RSA-PKCS-PSS -i data -o data.sig
-```
+```
To verify the signature:
```
@@ -118,14 +118,14 @@ This is a raw ECDSA signature, which is usually used to sign a hashed message. `
To sign the data:
```
-$ pkcs11-tool --id 11 --sign --pin 648219 --mechanism ECDSA -i data.sha1 -o data.sig --signature-format openssl
+$ pkcs11-tool --id 11 --sign --pin 648219 --mechanism ECDSA -i data.sha1 -o data.sig --signature-format openssl
Using slot 0 with a present token (0x0)
Using signature algorithm ECDSA
```
To verify the signature:
```
-$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
+$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
Signature Verified Successfully
```
@@ -143,6 +143,6 @@ Using signature algorithm ECDSA-SHA256
The signature is verified with the hash:
```
-$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
+$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
Signature Verified Successfully
```
diff --git a/doc/store_data.md b/doc/store_data.md
index 66b1d21..eb5a8f9 100644
--- a/doc/store_data.md
+++ b/doc/store_data.md
@@ -9,7 +9,7 @@ Before writting a file into the Pico HSM, we generate the data file with the fol
```
$ echo 'Pico HSM is awesome!' > test
-```
+```
Then, we can store the data file with the following command:
@@ -43,7 +43,7 @@ Always provide a unique `--label`, as it will be used to index and reference the
To view the stored file, we can use the following command with the same label we employed:
```
-$ pkcs11-tool --read-object --type data --label 'test1'
+$ pkcs11-tool --read-object --type data --label 'test1'
Using slot 0 with a present token (0x0)
Pico HSM is awesome!
```
@@ -98,7 +98,7 @@ Data object 'test1'
applicationName: test1
Path: e82b0601040181c31f0201::cf00
Data (21 bytes): 5069636F2048534D20697320617765736F6D65210A
-
+
Data object 'test2'
applicationName: test2
Path: e82b0601040181c31f0201::cd01
diff --git a/doc/usage.md b/doc/usage.md
index e06e776..a4d65e4 100644
--- a/doc/usage.md
+++ b/doc/usage.md
@@ -1,7 +1,7 @@
# Usage
## Tools
-We use multiple tools and PKCS#11 drivers and modules, depending on the purpose.
+We use multiple tools and PKCS#11 drivers and modules, depending on the purpose.
* **pkcs11-tool**: from OpenSC. It interfaces with the HSM via PKCS#11 interface. It supports different drivers and modules.
* **sc-tool**: an alias of pkcs11-tool with the sc-hsm-embedded module. It is mainly used for AES management and it is defined as:
```
@@ -32,10 +32,10 @@ The first step is to initialize the HSM:
```
$ sc-hsm-tool --initialize --so-pin 3537363231383830 --pin 648219
```
-The PIN number is used to manage all private keys in the device. It supports three attemps. After the third PIN failure, it gets blocked.
+The PIN number is used to manage all private keys in the device. It supports three attemps. After the third PIN failure, it gets blocked.
The PIN accepts from 6 to 16 characters.
-The SO-PIN is used to unblock the PIN. It accepts 15 attemps. After 15 failed attempts, the device will be completely blocked and will be necessary to initialize again, erasing all private keys and losing the access. Therefore, keep the SO-PIN in a safe place.
+The SO-PIN is used to unblock the PIN. It accepts 15 attemps. After 15 failed attempts, the device will be completely blocked and will be necessary to initialize again, erasing all private keys and losing the access. Therefore, keep the SO-PIN in a safe place.
The SO-PIN is always 16 hexadecimal characters.
## PIN and SO-PIN management
@@ -62,7 +62,7 @@ To generate a RSA 2048 bits, use the following command:
$ pkcs11-tool -l --pin 648219 --keypairgen --key-type rsa:2048 --id 1 --label "RSA2K"
Using slot 0 with a present token (0x0)
Key pair generated:
-Private Key Object; RSA
+Private Key Object; RSA
label: RSA2K
ID: 1
Usage: decrypt, sign
@@ -77,7 +77,7 @@ The ID parameter is an internal hexadecimal number for easy identification. The
Pico HSM accepts RSA of 1024 (`rsa:1024`), 2048 (`rsa:2048`) and 4096 bits (`rsa:4096`).
-**Caution**: RSA 2048 bits may take more than 20 seconds. RSA 4096 bits may take more than 20 minutes. The Pico HSM will work as normally and neither the HSM nor the host will block. But, in the meantime, the Pico HSM will not accept any command.
+**Caution**: RSA 2048 bits may take more than 20 seconds. RSA 4096 bits may take more than 20 minutes. The Pico HSM will work as normally and neither the HSM nor the host will block. But, in the meantime, the Pico HSM will not accept any command.
An alternative is to generate the private key locally and import it to the HSM. This approach, however, is less secure as it does not use a True RNG or HRNG like Pico HSM. Use this approach if you have plugged a TRNG or you are not worried about obtaining the highest entropy.
Pico HSM also accepts ECDSA keypairs:
@@ -157,9 +157,9 @@ Certificate:
a0:30:b2:ec:d3:d6:0d:58:f3
Exponent: 65537 (0x10001)
X509v3 extensions:
- X509v3 Subject Key Identifier:
+ X509v3 Subject Key Identifier:
98:07:DA:13:B0:8E:A0:5C:97:83:68:FE:4A:25:8D:50:C4:DC:16:FA
- X509v3 Authority Key Identifier:
+ X509v3 Authority Key Identifier:
keyid:98:07:DA:13:B0:8E:A0:5C:97:83:68:FE:4A:25:8D:50:C4:DC:16:FA
X509v3 Basic Constraints: critical
@@ -173,7 +173,7 @@ Certificate:
99:2b:b2:82:66:c1:06:a7:2c:62:af:e2:e4:93:42:36:66:8d:
c5:3f:e1:ec:5f:9a:f8:5f:b3:6a:8f:0e:12:5d:c9:46:38:ea:
0b:08
-```
+```
The resulting file `cert.pem` contains the signed certificate in PEM format. Convert it into DER format and load it into the Pico HSM:
diff --git a/patch_vidpid.sh b/patch_vidpid.sh
index 0ec3ffb..ea47f29 100755
--- a/patch_vidpid.sh
+++ b/patch_vidpid.sh
@@ -1,19 +1,19 @@
#!/bin/bash
-#
+#
# This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
# Copyright (c) 2022 Pol Henarejos.
-#
-# This program is free software: you can redistribute it and/or modify
-# it under the terms of the GNU General Public License as published by
+#
+# This program is free software: you can redistribute it and/or modify
+# it under the terms of the GNU General Public License as published by
# the Free Software Foundation, version 3.
#
-# This program is distributed in the hope that it will be useful, but
-# WITHOUT ANY WARRANTY; without even the implied warranty of
-# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+# This program is distributed in the hope that it will be useful, but
+# WITHOUT ANY WARRANTY; without even the implied warranty of
+# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
# General Public License for more details.
#
-# You should have received a copy of the GNU General Public License
+# You should have received a copy of the GNU General Public License
# along with this program. If not, see
@@ -64,17 +64,17 @@ From now on, you have full access and can operate normally with the primary devi
Pico HSM uses the PIN to protect the DKEK, which is lately used to protect private/secret keys and wrap/unwrap. However, when PKA is enabled, the authentication is not performed by introducing any PIN.
Authenticated privileges are granted when PKA succeeds, regardless of PIN, which is optional.
-Nevertheless, **it is extremely recommended to combine PKA with PIN**. Note that when combined, only PKA grants authenticated privileges. Therefore, if both schemes are setup, it is necessary to unlock the DKEK with PIN verification.
+Nevertheless, **it is extremely recommended to combine PKA with PIN**. Note that when combined, only PKA grants authenticated privileges. Therefore, if both schemes are setup, it is necessary to unlock the DKEK with PIN verification.
Otherwise, it will not be possible to operate with private/secret keys despite the user will be logged in.
With this scheme, multiple custodians may authenticate the device individually and remotely and, when fully authenticated, the master user can unlock the DKEK with the PIN.
-Moreover, with this approach the device is kept safe and neither the DKEK nor the private/secret keys are stored in plain text in the device.
+Moreover, with this approach the device is kept safe and neither the DKEK nor the private/secret keys are stored in plain text in the device.
Even though the flash memory is dumped by an attacker, it will not be possible to decipher any sensitive data or key.
Initialization of the device with PKA **and** PIN can be achieved with SCS3 or OpenSC:
-**Note:** do not import any DKEK share or DKEK operation before PKA and PIN setup.
+**Note:** do not import any DKEK share or DKEK operation before PKA and PIN setup.
### With OpenSC
@@ -84,9 +84,9 @@ Use the following command (or similar), which accepts the use of PIN parameter *
sc-hsm-tool -X --so-pin 1234567890123456 --pin 648219 -K 1 -n 1 -s 1
```
-and PKA and PIN are enabled, jointly with DKEK protection.
+and PKA and PIN are enabled, jointly with DKEK protection.
-### With SCS3
+###�With SCS3
Unfortunately, SCS3 does not allow to initialize the device with PKA and PIN at the same time, though it can be achieved in separated steps:
@@ -94,4 +94,4 @@ Unfortunately, SCS3 does not allow to initialize the device with PKA and PIN at
2. There is NO default PIN. So, DO NOT attempt to log in yet. A reset PIN shall be requested.
3. Click on ``Reset User-PIN``, introduce the SO-PIN configured during the initialization and introduce the desired User-PIN.
-When done, the device will be configured with PIN **and** PKA.
+When done, the device will be configured with PIN **and** PKA.
diff --git a/doc/scs3.md b/doc/scs3.md
index 92573e1..8dd9dbe 100644
--- a/doc/scs3.md
+++ b/doc/scs3.md
@@ -4,11 +4,11 @@ SCS3 tool is a specific tool developed by CardContact to manage HSM. Thanks to i
- Import PKCS12 private keys and certificates.
- Import private keys and certificates from other Pico HSM devices in WKY format.
--
+-
Unfortunately, there is no pkcs11 tool or equivalent capable to perform the import. Since it uses the SC-HSM driver, it also supports the communication with the [SCS3 tool](https://www.openscdp.org/scsh3/ "SCS3 tool"). It can be downloaded from [here](https://www.openscdp.org/scsh3/download.html "here").
-However, SCS3 only works with those HSM manufactured by CardContact. The check is performed by means of trust store against the manufacturing certificates. For obvious reasons, these certificates can only be signed with the private keys of the Certificate Authorities listed in the trust store.
+However, SCS3 only works with those HSM manufactured by CardContact. The check is performed by means of trust store against the manufacturing certificates. For obvious reasons, these certificates can only be signed with the private keys of the Certificate Authorities listed in the trust store.
Pico HSM is shipped with its own CA certificates. To load this certificate onto the trust store of SCS3, the following line has to be appended to `SmartCardHSM.rootCerts` variable, near line `235` in the file `scs3/scsh/sc-hsm/SmartCardHSM.js`.
@@ -39,8 +39,8 @@ After this ammendment, the program can be started and the KeyManager can be invo
>load("keymanager/keymanager.js");
SmartCard-HSM Version 1.6 on JCOP Free memory 217104 byte
-Issuer Certificate : CVC id-AT DV (official domestic) CAR=ESCVCAHSM00001 CHR=ESDVCAHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2025
-Device Certificate : CVC id-AT Terminal CAR=ESDVCAHSM00001 CHR=ESTERMHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2023
+Issuer Certificate : CVC id-AT DV (official domestic) CAR=ESCVCAHSM00001 CHR=ESDVCAHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2025
+Device Certificate : CVC id-AT Terminal CAR=ESDVCAHSM00001 CHR=ESTERMHSM00001 CED=27 / de març / 2022 CXD=31 / de desembre / 2023
Default Key Domain : 0F89B400975EDD2D425ABF85F2FBD318779B3D85475E65D4
-------------------------------------------------------------------
Please right-click on nodes in the outline to see possible actions.
@@ -60,7 +60,7 @@ It can be executed in a Terminal via
```
## DKEK requirement
-In order to perform the import, private keys must be wrapped with the same DKEK present in the Pico HSM. Thus, the Pico HSM must be previously initialized with at minimum of 1 DKEK share. This share will be used to wrap the private key before import.
+In order to perform the import, private keys must be wrapped with the same DKEK present in the Pico HSM. Thus, the Pico HSM must be previously initialized with at minimum of 1 DKEK share. This share will be used to wrap the private key before import.
Note that the DKEK share shall be available before the import. In this way, all custodians must be present during the import process, since they will have to introduce their respective DKEK.
diff --git a/doc/sign-verify.md b/doc/sign-verify.md
index 1c668e7..c7c1c93 100644
--- a/doc/sign-verify.md
+++ b/doc/sign-verify.md
@@ -1,7 +1,7 @@
# Sign and verify
Pico HSM supports in place signature of arbitrary data. It supports the following algorithms:
-* RSA-PKCS
+* RSA-PKCS
* RSA-X-509
* SHA1-RSA-PKCS
* SHA256-RSA-PKCS
@@ -32,7 +32,7 @@ $ openssl rsa -inform DER -outform PEM -in 1.der -pubin > 1.pub
At this moment, you are able to verify with the public key in `1.pub`. The signature is computed inside the Pico HSM with the private key. It never leaves the device.
## RSA-PKCS
-This algorithm is used to sign raw data.
+This algorithm is used to sign raw data.
To sign the data:
```
@@ -91,7 +91,7 @@ This algorithm uses the RSA-PKCS with PSS salt to randomize the signature. Pico
To sign the data:
```
$ pkcs11-tool --id 1 --sign --pin 648219 --mechanism RSA-PKCS-PSS -i data.sha1 -o data.sig
-```
+```
To verify the signature:
```
@@ -105,7 +105,7 @@ This algorithm takes the file as the input and sends its hash for signing with t
To sign the data:
```
$ pkcs11-tool --id 1 --sign --pin 648219 --mechanism SHA1-RSA-PKCS-PSS -i data -o data.sig
-```
+```
To verify the signature:
```
@@ -118,14 +118,14 @@ This is a raw ECDSA signature, which is usually used to sign a hashed message. `
To sign the data:
```
-$ pkcs11-tool --id 11 --sign --pin 648219 --mechanism ECDSA -i data.sha1 -o data.sig --signature-format openssl
+$ pkcs11-tool --id 11 --sign --pin 648219 --mechanism ECDSA -i data.sha1 -o data.sig --signature-format openssl
Using slot 0 with a present token (0x0)
Using signature algorithm ECDSA
```
To verify the signature:
```
-$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
+$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
Signature Verified Successfully
```
@@ -143,6 +143,6 @@ Using signature algorithm ECDSA-SHA256
The signature is verified with the hash:
```
-$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
+$ openssl pkeyutl -verify -pubin -inkey 11.pub -in data.sha1 -sigfile data.sig
Signature Verified Successfully
```
diff --git a/doc/store_data.md b/doc/store_data.md
index 66b1d21..eb5a8f9 100644
--- a/doc/store_data.md
+++ b/doc/store_data.md
@@ -9,7 +9,7 @@ Before writting a file into the Pico HSM, we generate the data file with the fol
```
$ echo 'Pico HSM is awesome!' > test
-```
+```
Then, we can store the data file with the following command:
@@ -43,7 +43,7 @@ Always provide a unique `--label`, as it will be used to index and reference the
To view the stored file, we can use the following command with the same label we employed:
```
-$ pkcs11-tool --read-object --type data --label 'test1'
+$ pkcs11-tool --read-object --type data --label 'test1'
Using slot 0 with a present token (0x0)
Pico HSM is awesome!
```
@@ -98,7 +98,7 @@ Data object 'test1'
applicationName: test1
Path: e82b0601040181c31f0201::cf00
Data (21 bytes): 5069636F2048534D20697320617765736F6D65210A
-
+
Data object 'test2'
applicationName: test2
Path: e82b0601040181c31f0201::cd01
diff --git a/doc/usage.md b/doc/usage.md
index e06e776..a4d65e4 100644
--- a/doc/usage.md
+++ b/doc/usage.md
@@ -1,7 +1,7 @@
# Usage
## Tools
-We use multiple tools and PKCS#11 drivers and modules, depending on the purpose.
+We use multiple tools and PKCS#11 drivers and modules, depending on the purpose.
* **pkcs11-tool**: from OpenSC. It interfaces with the HSM via PKCS#11 interface. It supports different drivers and modules.
* **sc-tool**: an alias of pkcs11-tool with the sc-hsm-embedded module. It is mainly used for AES management and it is defined as:
```
@@ -32,10 +32,10 @@ The first step is to initialize the HSM:
```
$ sc-hsm-tool --initialize --so-pin 3537363231383830 --pin 648219
```
-The PIN number is used to manage all private keys in the device. It supports three attemps. After the third PIN failure, it gets blocked.
+The PIN number is used to manage all private keys in the device. It supports three attemps. After the third PIN failure, it gets blocked.
The PIN accepts from 6 to 16 characters.
-The SO-PIN is used to unblock the PIN. It accepts 15 attemps. After 15 failed attempts, the device will be completely blocked and will be necessary to initialize again, erasing all private keys and losing the access. Therefore, keep the SO-PIN in a safe place.
+The SO-PIN is used to unblock the PIN. It accepts 15 attemps. After 15 failed attempts, the device will be completely blocked and will be necessary to initialize again, erasing all private keys and losing the access. Therefore, keep the SO-PIN in a safe place.
The SO-PIN is always 16 hexadecimal characters.
## PIN and SO-PIN management
@@ -62,7 +62,7 @@ To generate a RSA 2048 bits, use the following command:
$ pkcs11-tool -l --pin 648219 --keypairgen --key-type rsa:2048 --id 1 --label "RSA2K"
Using slot 0 with a present token (0x0)
Key pair generated:
-Private Key Object; RSA
+Private Key Object; RSA
label: RSA2K
ID: 1
Usage: decrypt, sign
@@ -77,7 +77,7 @@ The ID parameter is an internal hexadecimal number for easy identification. The
Pico HSM accepts RSA of 1024 (`rsa:1024`), 2048 (`rsa:2048`) and 4096 bits (`rsa:4096`).
-**Caution**: RSA 2048 bits may take more than 20 seconds. RSA 4096 bits may take more than 20 minutes. The Pico HSM will work as normally and neither the HSM nor the host will block. But, in the meantime, the Pico HSM will not accept any command.
+**Caution**: RSA 2048 bits may take more than 20 seconds. RSA 4096 bits may take more than 20 minutes. The Pico HSM will work as normally and neither the HSM nor the host will block. But, in the meantime, the Pico HSM will not accept any command.
An alternative is to generate the private key locally and import it to the HSM. This approach, however, is less secure as it does not use a True RNG or HRNG like Pico HSM. Use this approach if you have plugged a TRNG or you are not worried about obtaining the highest entropy.
Pico HSM also accepts ECDSA keypairs:
@@ -157,9 +157,9 @@ Certificate:
a0:30:b2:ec:d3:d6:0d:58:f3
Exponent: 65537 (0x10001)
X509v3 extensions:
- X509v3 Subject Key Identifier:
+ X509v3 Subject Key Identifier:
98:07:DA:13:B0:8E:A0:5C:97:83:68:FE:4A:25:8D:50:C4:DC:16:FA
- X509v3 Authority Key Identifier:
+ X509v3 Authority Key Identifier:
keyid:98:07:DA:13:B0:8E:A0:5C:97:83:68:FE:4A:25:8D:50:C4:DC:16:FA
X509v3 Basic Constraints: critical
@@ -173,7 +173,7 @@ Certificate:
99:2b:b2:82:66:c1:06:a7:2c:62:af:e2:e4:93:42:36:66:8d:
c5:3f:e1:ec:5f:9a:f8:5f:b3:6a:8f:0e:12:5d:c9:46:38:ea:
0b:08
-```
+```
The resulting file `cert.pem` contains the signed certificate in PEM format. Convert it into DER format and load it into the Pico HSM:
diff --git a/patch_vidpid.sh b/patch_vidpid.sh
index 0ec3ffb..ea47f29 100755
--- a/patch_vidpid.sh
+++ b/patch_vidpid.sh
@@ -1,19 +1,19 @@
#!/bin/bash
-#
+#
# This file is part of the Pico HSM distribution (https://github.com/polhenarejos/pico-hsm).
# Copyright (c) 2022 Pol Henarejos.
-#
-# This program is free software: you can redistribute it and/or modify
-# it under the terms of the GNU General Public License as published by
+#
+# This program is free software: you can redistribute it and/or modify
+# it under the terms of the GNU General Public License as published by
# the Free Software Foundation, version 3.
#
-# This program is distributed in the hope that it will be useful, but
-# WITHOUT ANY WARRANTY; without even the implied warranty of
-# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
+# This program is distributed in the hope that it will be useful, but
+# WITHOUT ANY WARRANTY; without even the implied warranty of
+# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
# General Public License for more details.
#
-# You should have received a copy of the GNU General Public License
+# You should have received a copy of the GNU General Public License
# along with this program. If not, see